Stealtwatch admin access via Tacacs+ protocol is quite easy in configuration. Below short instruction how you to create full access for administrators.
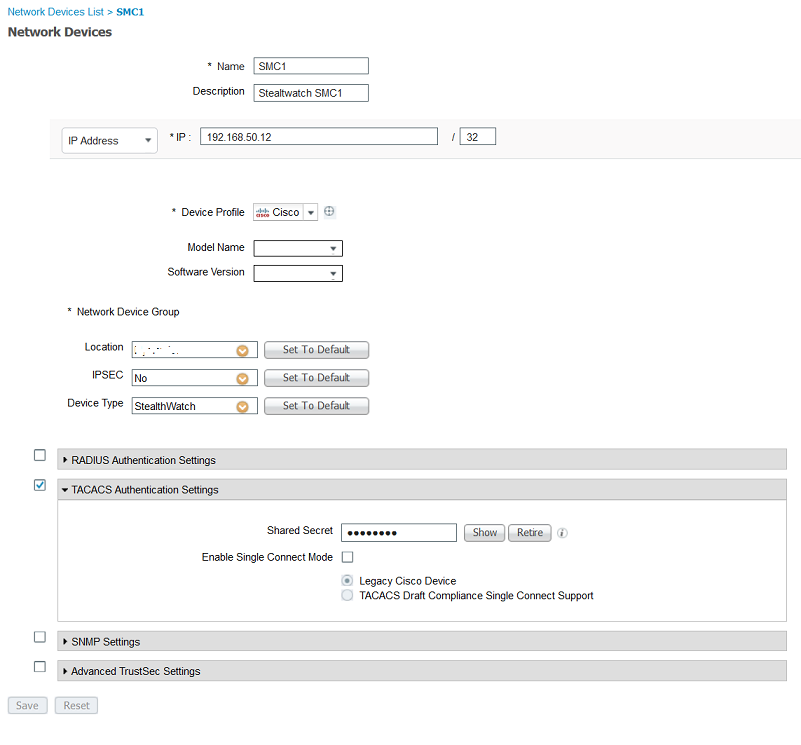
- Configure Stealthwatch SMC as a tacacs+ client(NAD) in ISE
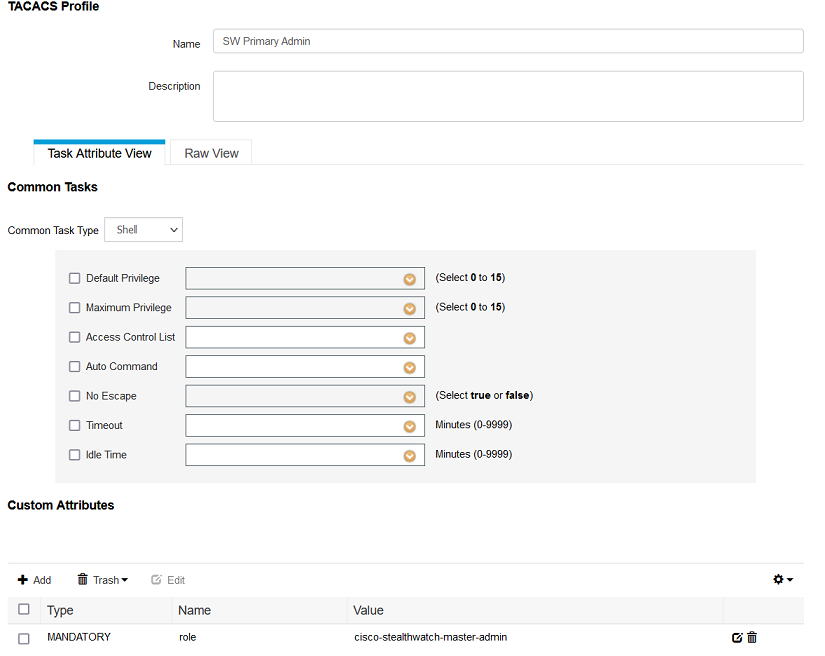
- Configure Tacacs Profiles for StealthWatch roles (in our case full access)
- Create policy sets for StealtWatch access
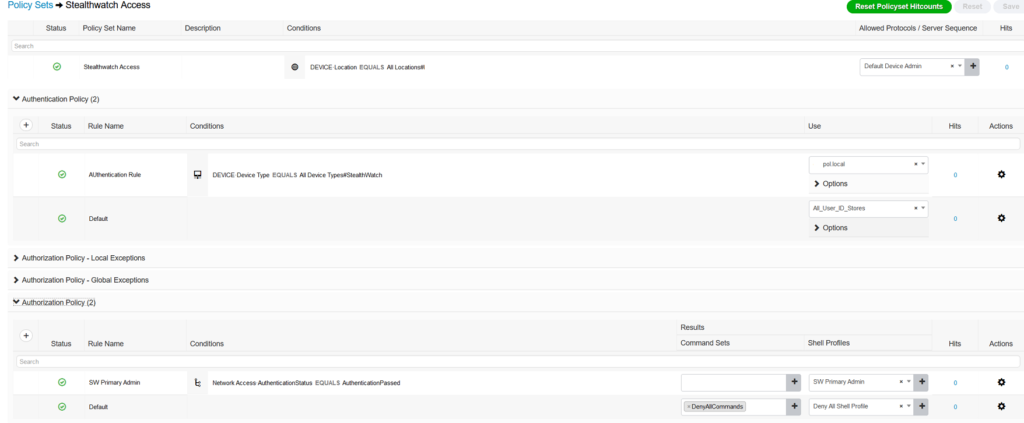
Our rules are very simple. In auth user verification in domain, in authz if authentication passed then assign SW primary Admin profile.
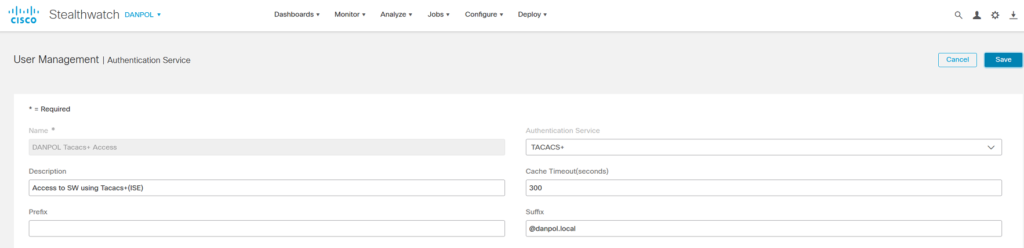
- Configure TACACS+ in StealthWatch
Go to Global Settings – User Management – Authentication and Authorization TAB and create Tacacs server
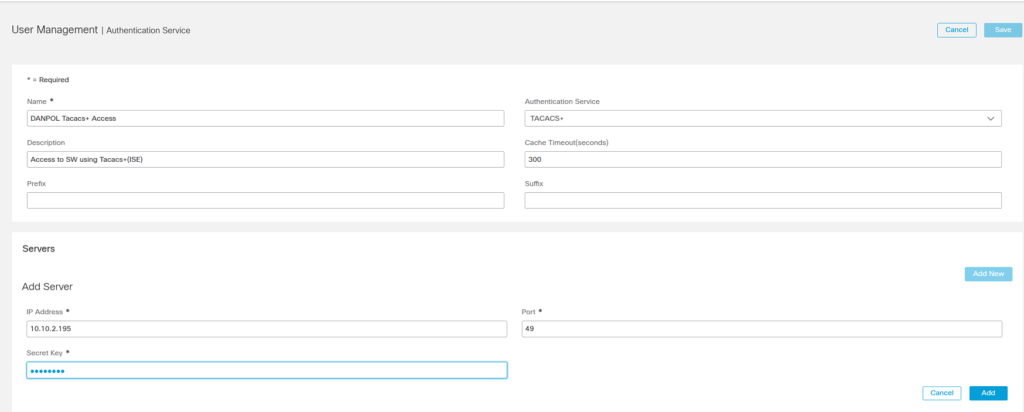
Select Protocol to tacacs+ , add server IP(s) and click “Add” and next “Save”.
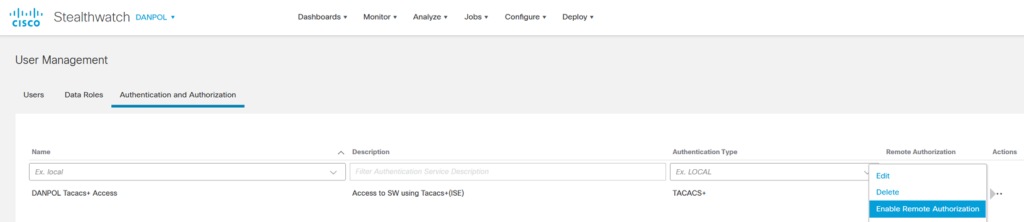
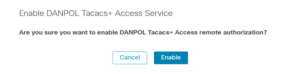
Enable Tacacs AAA in SW (Enable Remote Authorization).
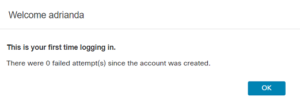
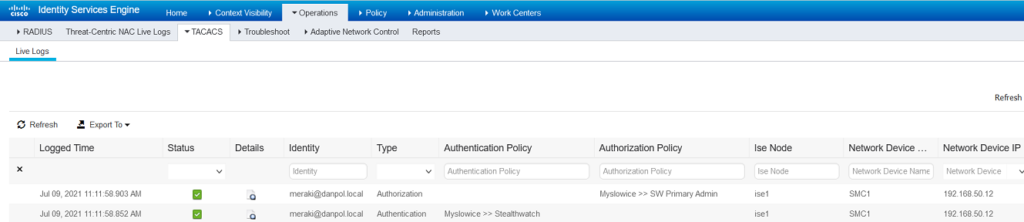
- Test Access to SW using user(s) authenticated via ISE, in my case AD user.
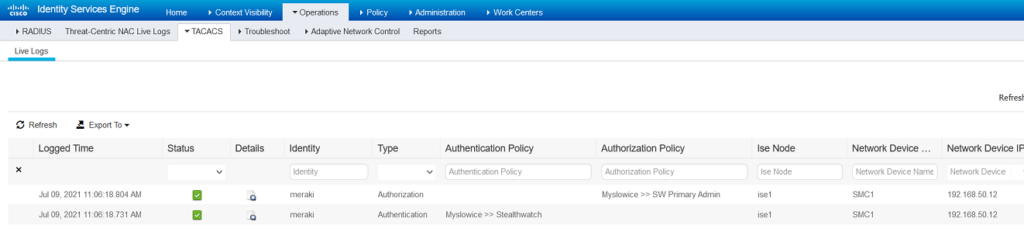
view from SW

View from ISE
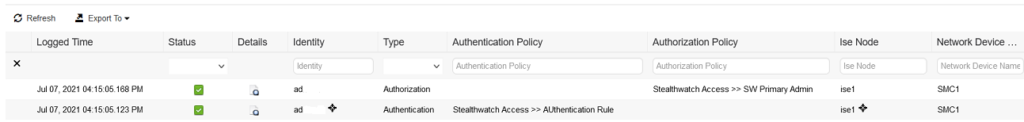
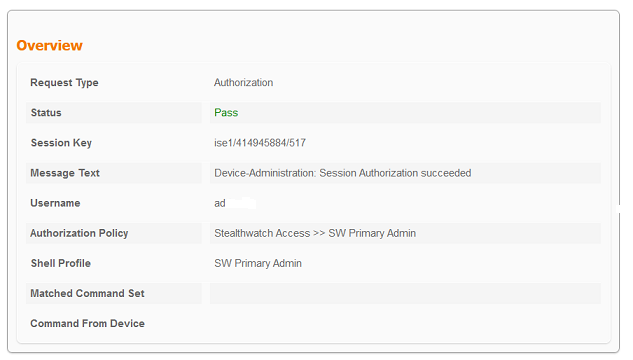
and below role assigned to our tacacs+ user
![]()
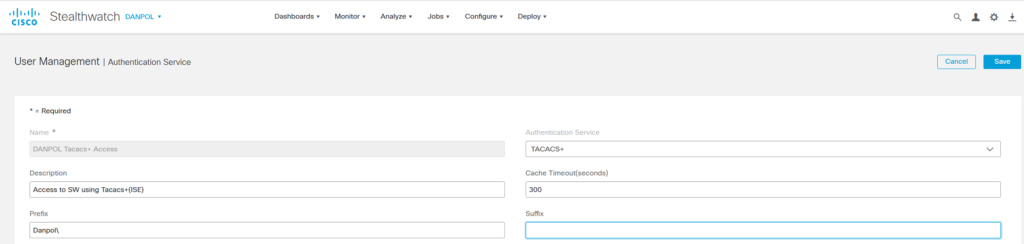
- Prefix and Suffix
StealtWatch has inbuilt 2 options to automatically add domain prefix or suffix.
The difference between thouse is the following:
– when we specify prefix,eg. “Danpol\” and user is logging into SW then system is adding “Danpol\” domain automatically to username.
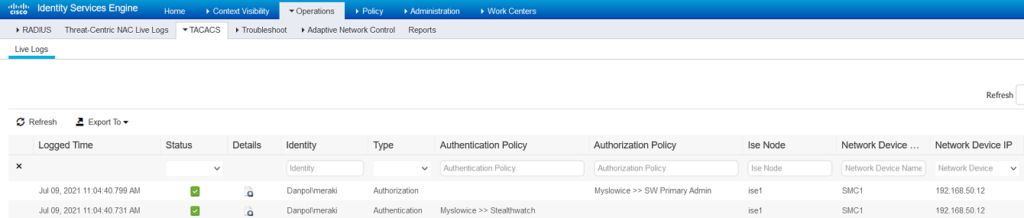
– when we specify prefix,eg. “@danpol.local” and user is logging into SW, then system is adding Danpol domain automatically to username.
Please note, the same results we can achieve typing domain\username or username@domain in log on screen.
07-07-2021