There are few possibilities how to authenticate and authorized admin users in ISE. First, and the most common way, is to use internal admin users. Second, also quite common way, is to use Active Directory users, especially most of ISE deployments is already integrated with AD for network access.
Another option is to use external Radius servers with OTP password like SafeWord or similar solution. What in case we do not have OTP providers but we want to use different user databases,eg. AD users integrated with different ISE deployment? It is still possible and configuration is quite easy.
Below configuration:
ISE1 – ISE deployment where we need admin access using users authenticated in different user database(AD)
ISE2 – Radius server. It can be any radius server,e.g Microsoft, Linux,etc. The only thing what we need from that server is information “Access-Accept or “Access-Reject”.
ISE2 Configuration
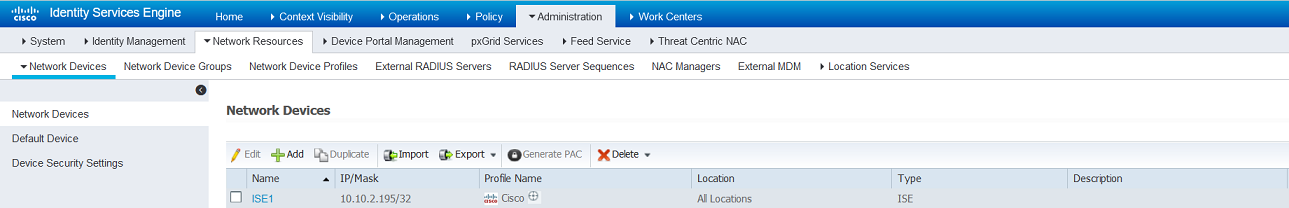
- create typical network access device(NAD)
- Create policy set (in my scenario I use device type = ISE as a condition
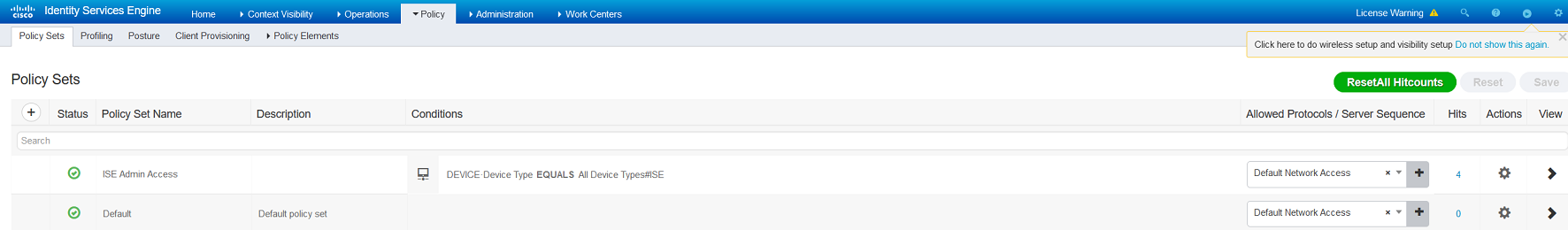
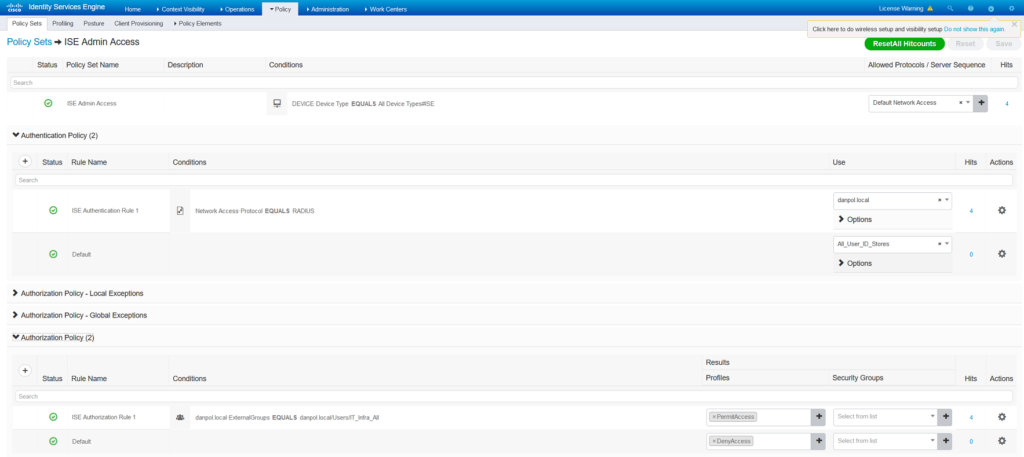
Authentication and Authorizaiton conditions configure based on your security requirements but for this example I am checking if user belongs to Active Directory group “IT_Infra_All.
ISE1 Configuration
- Configure Radius Token Identity Source
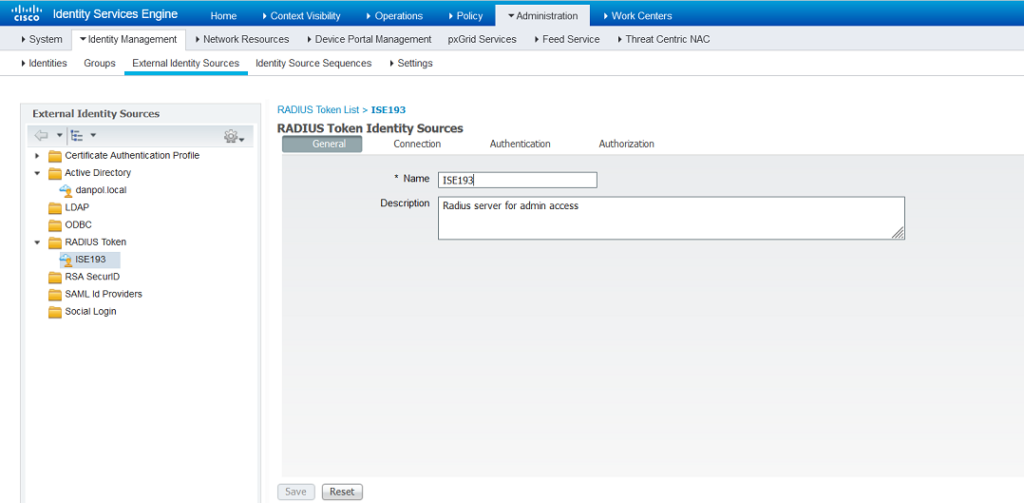
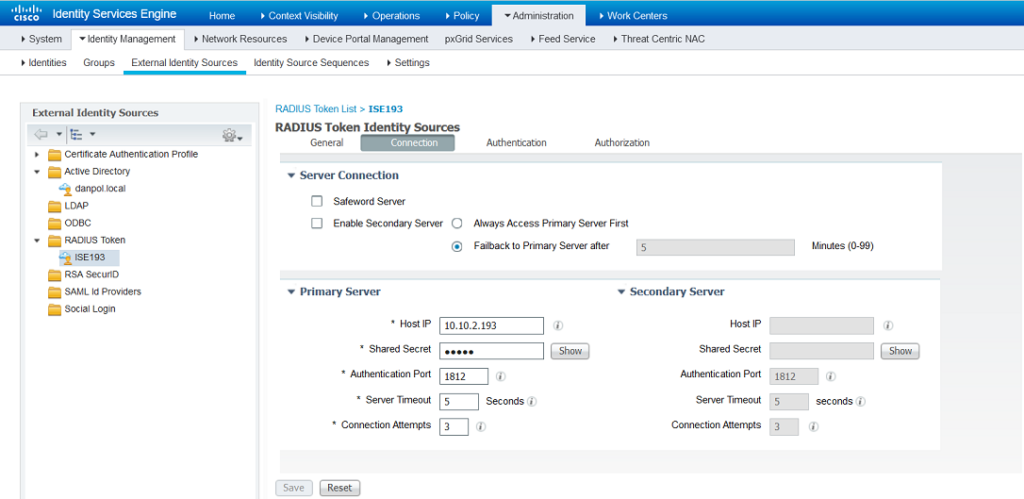
Configure secondary radius server, if needed.
- Confi
- Configure Admin Access Authentication Method to previously created radius Token Identity Source (RADIUS:ISE193)
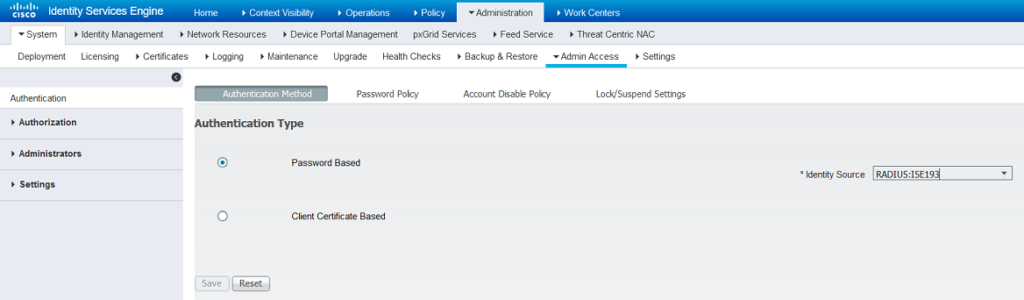
- Create admin users with external authentication with appropiate access level( in my scenario “Super Admins” and “HelpDesk Admin”.
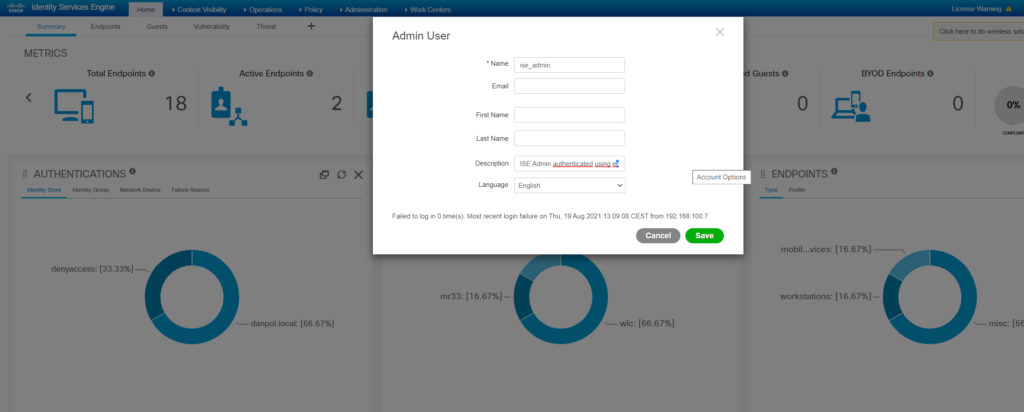
ISE using external radius server for admin access authenticate users on external/remote radius server however authorization is checked locally. Due to that fact it is necessary to create admin users in local ISE(no password needed – password is checked on external radius server). Username must be the same as in external database.
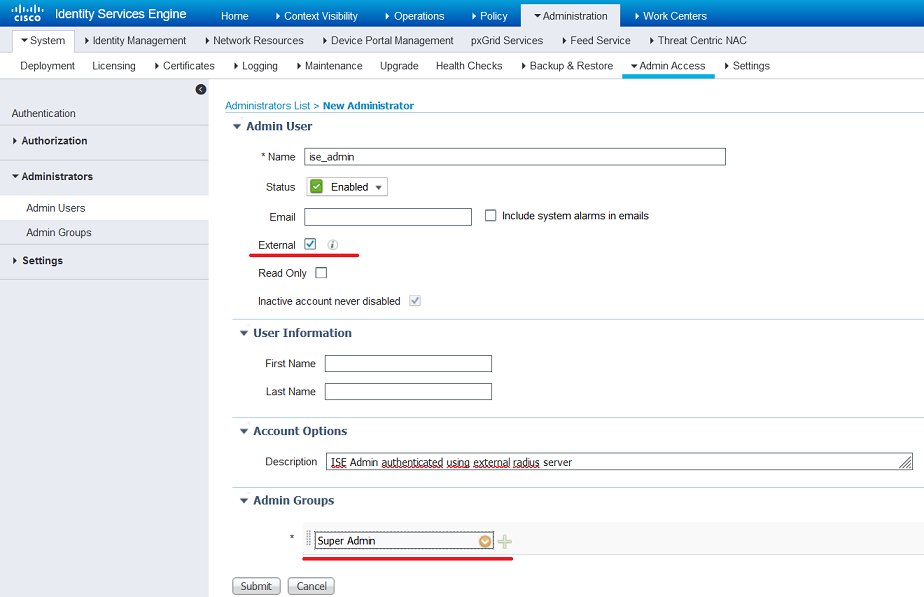
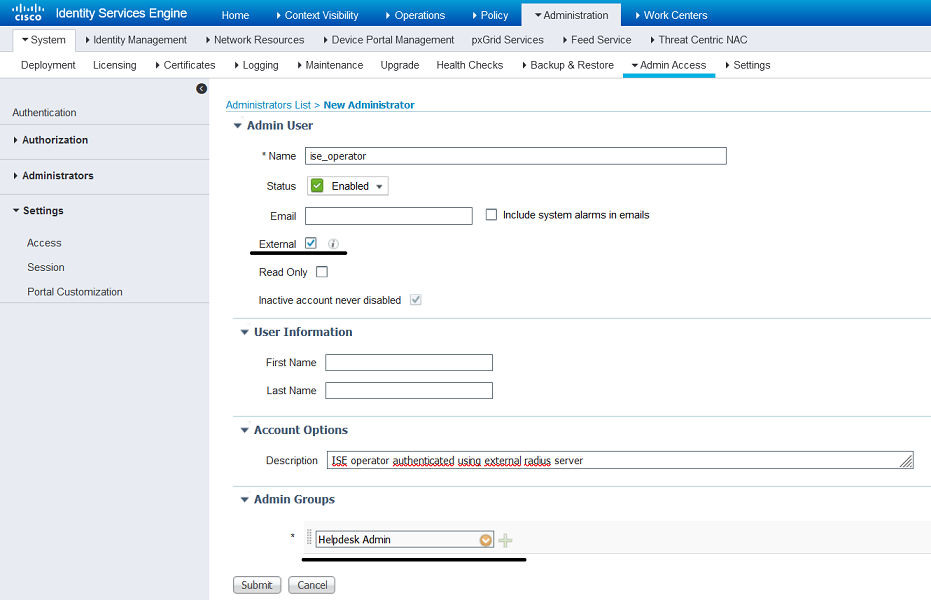
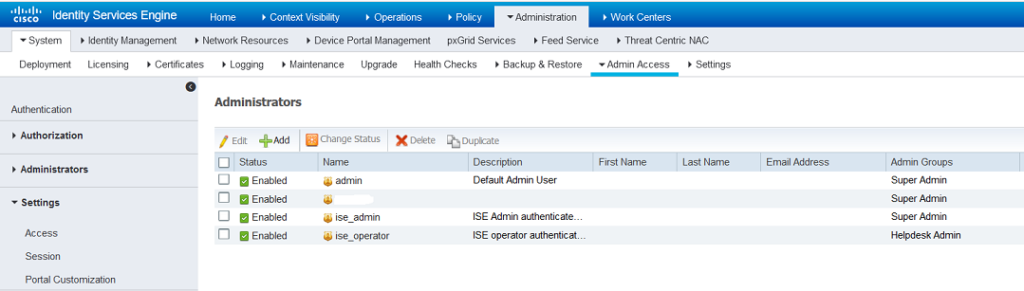
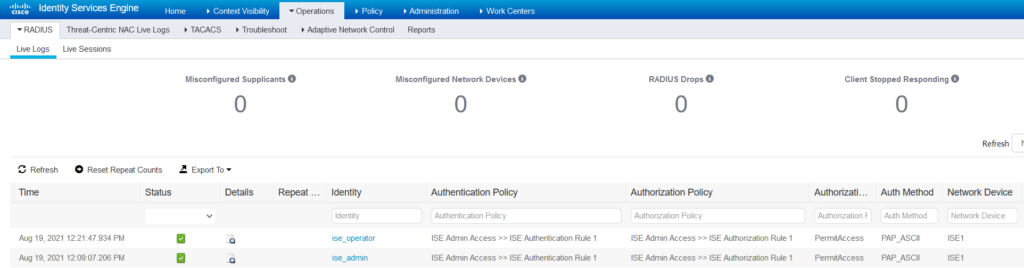
Verification
- ISE Admin
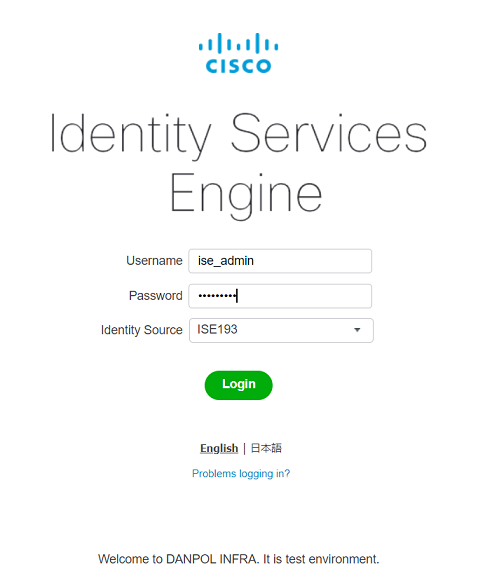
Logs – external radius server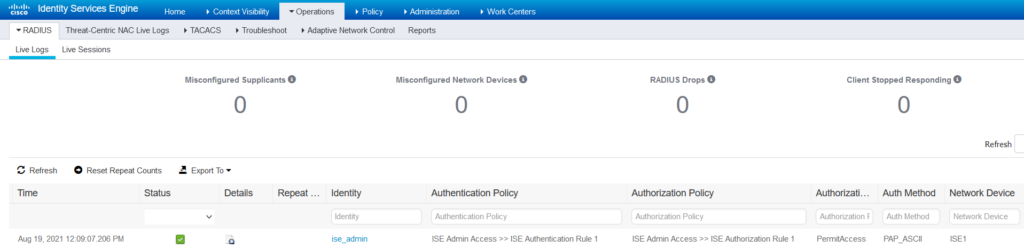
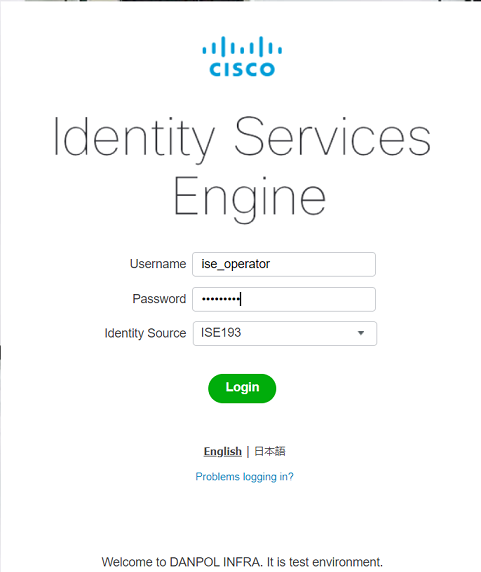
- ISE Operator
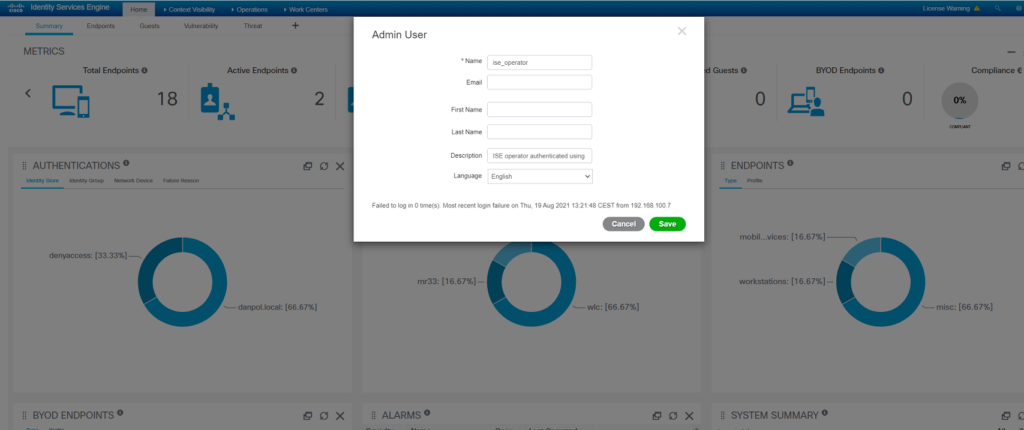 Logs – exernal radius server
Logs – exernal radius server