Goals:
- 2 Realms ( 2 Active Directory domains/separate forest)
- Use AD groups/user for traffic enforcement
1. Create realms (Go to Integration –> Realms)
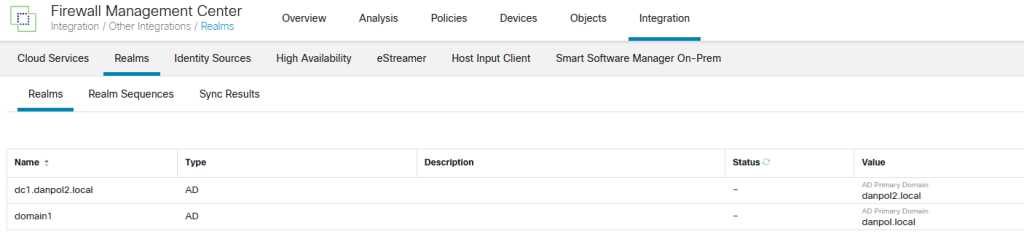
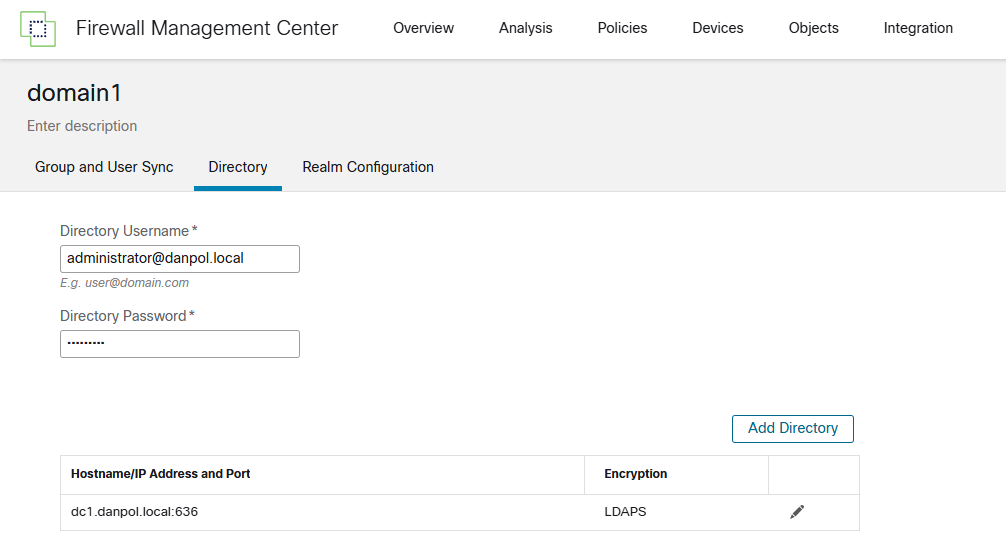
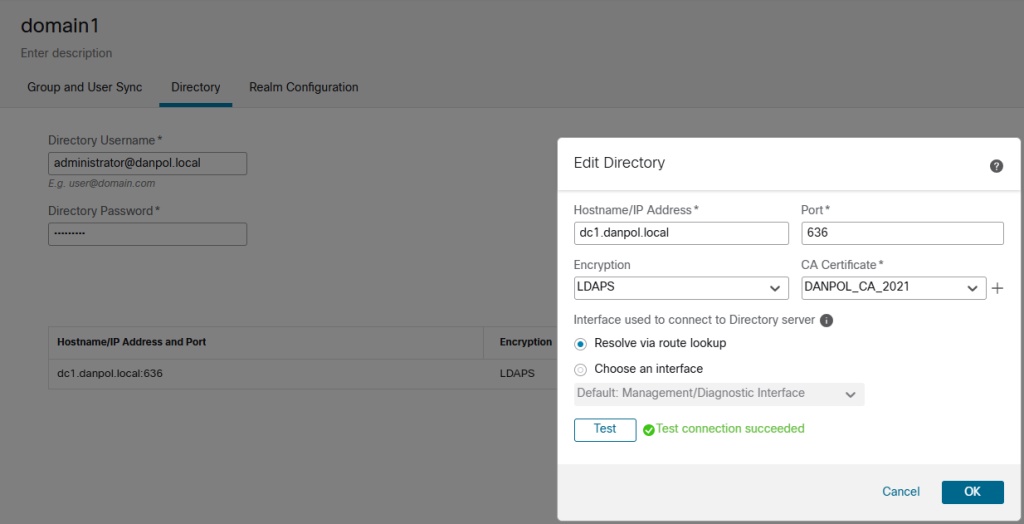
- first domain/forest – configure access to domain1 and test connection to domain controller
- specify what groups you want to include/exclude in passive authentication
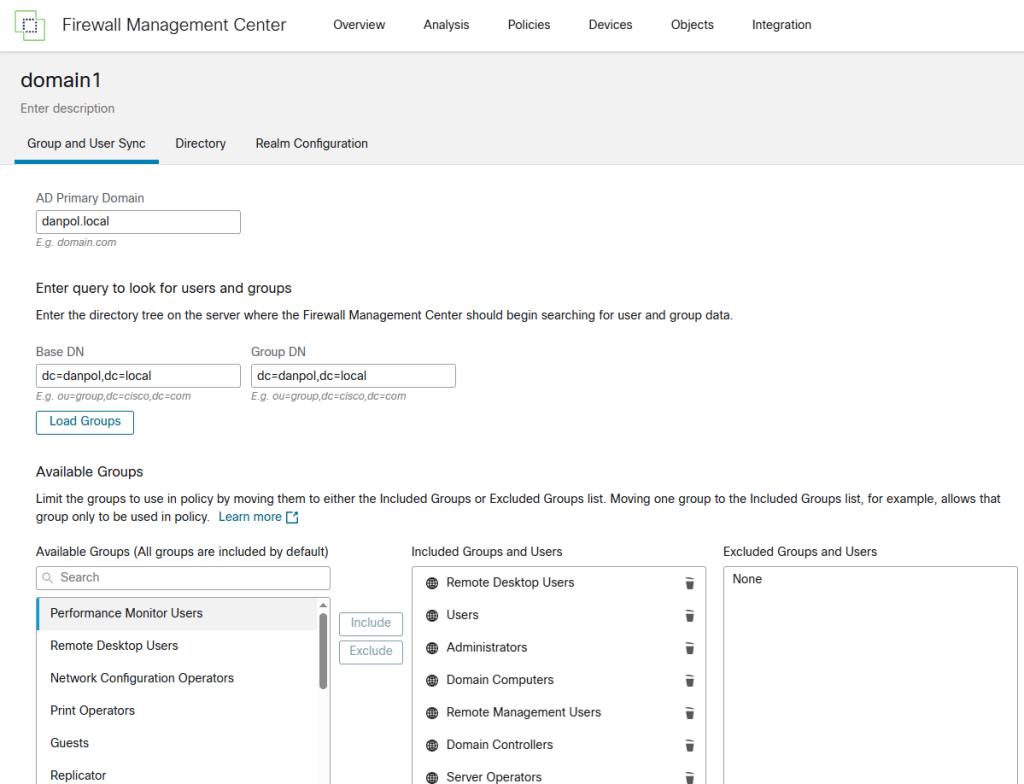
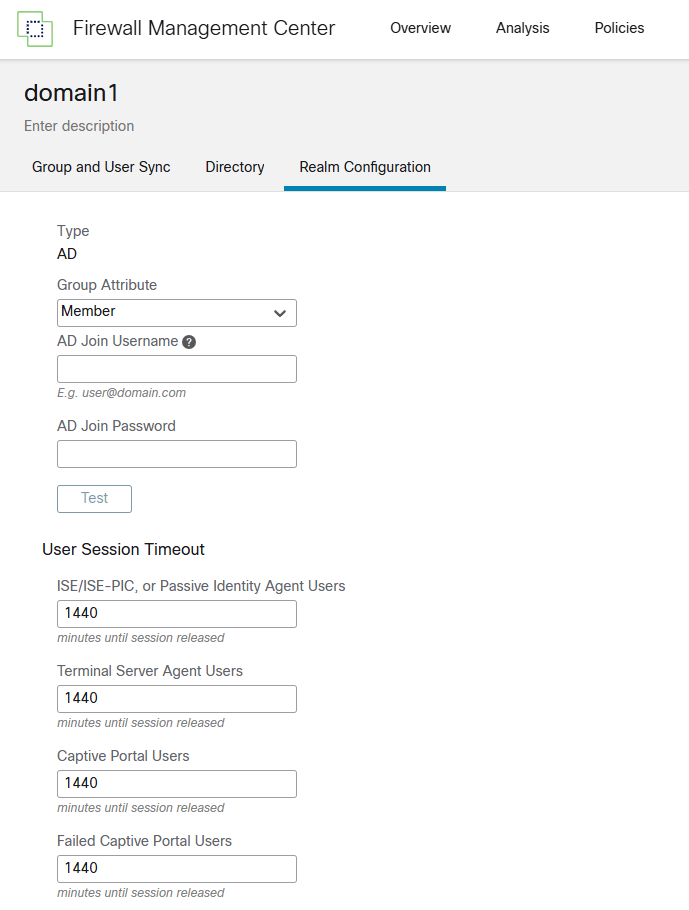
- repeat the same step for second domain/realm.
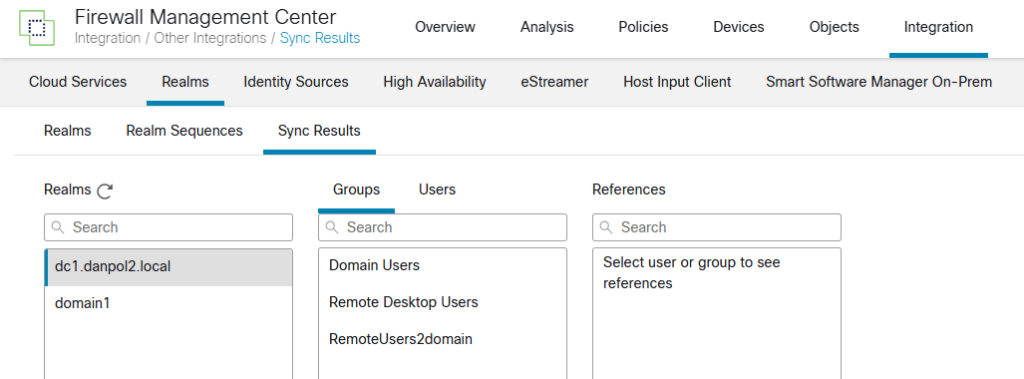
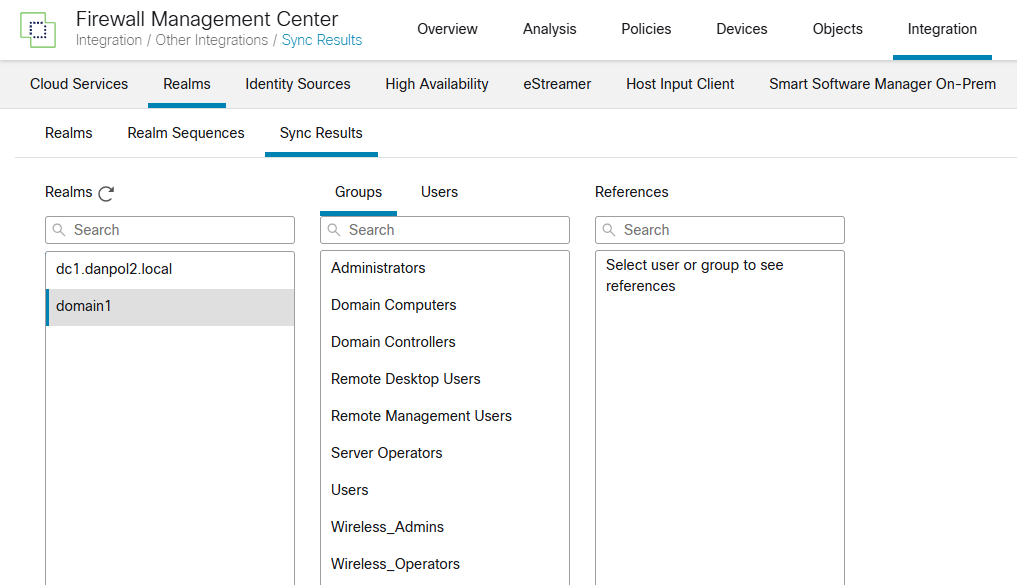
- verify what groups/users are synced with domains
2.Create Passive Identity Agent under Integration –> Identity Sources –> Passive Identity Agent
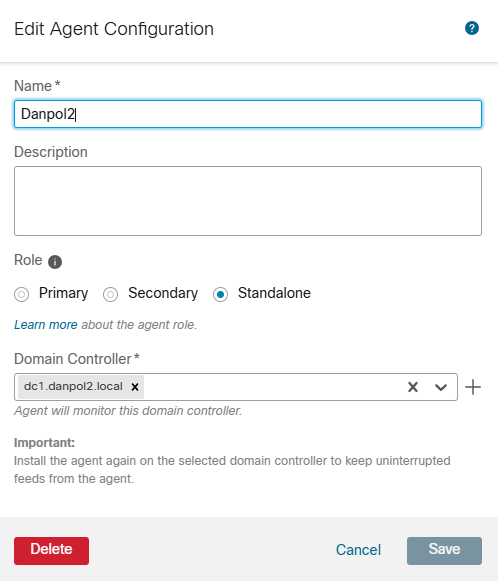
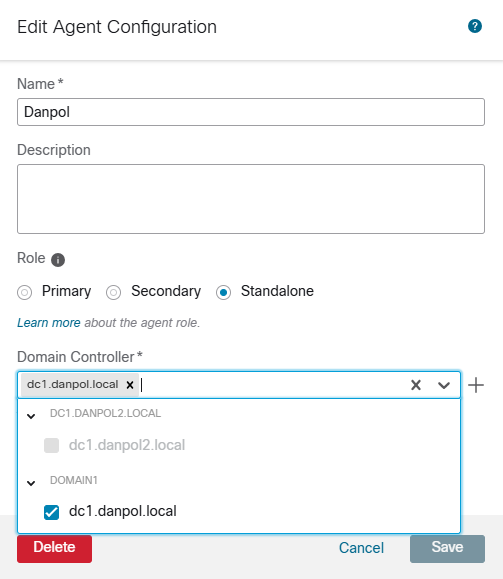
I selected standalone agent but in production environment you should use 2 passive identity agents (primary & secondary).
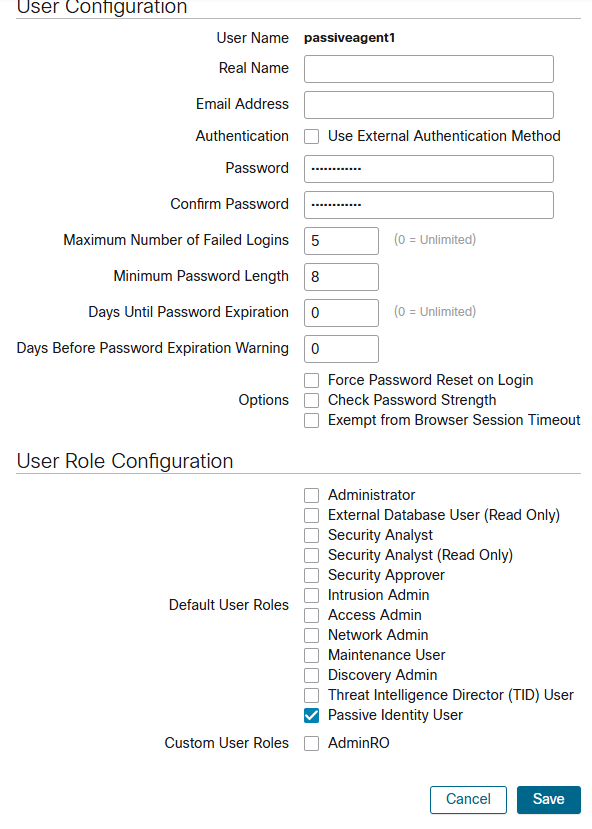
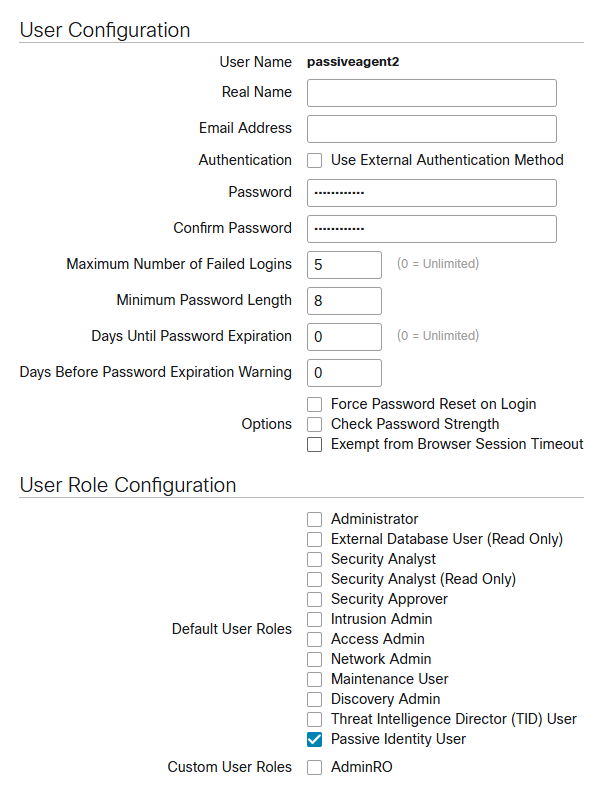
3.Create users responsible for exchanging data with agent installed in domains (in my case on domain controller)
4.Install passive ID agent on hosts withing particular domain (type FMC,port, username/password you previously created and select realm).
Test connection and if all is OK save configuration.
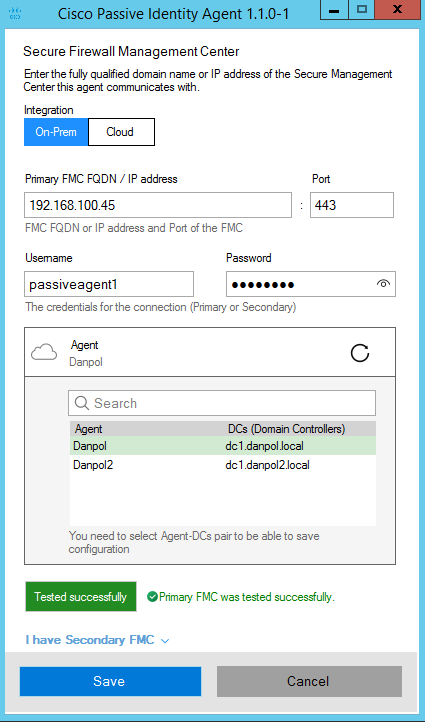
Repeat the same step in second domain using different user and domain.
When all is configured properly you should see connection status in green in “Passive Identity Agent” tab
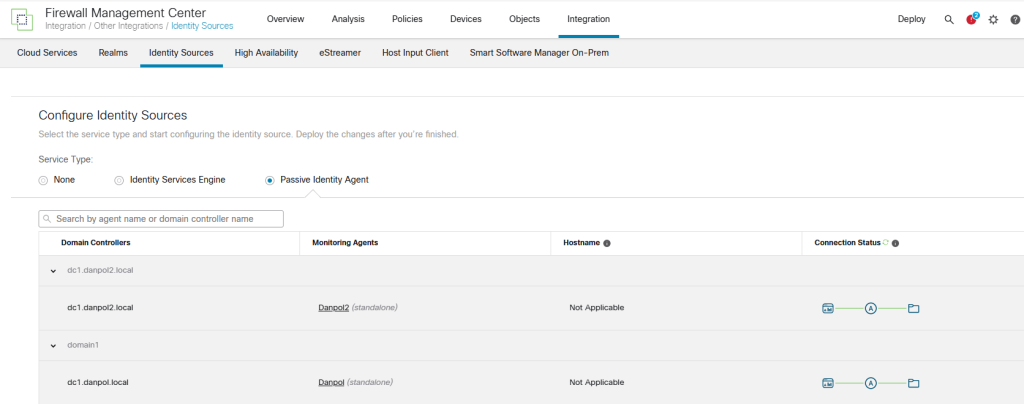
5. Verify passive authentication status (Go to Analysis –> Users –> Active Sessions). You should see entries when user log in to PC in domain nearly in real time.
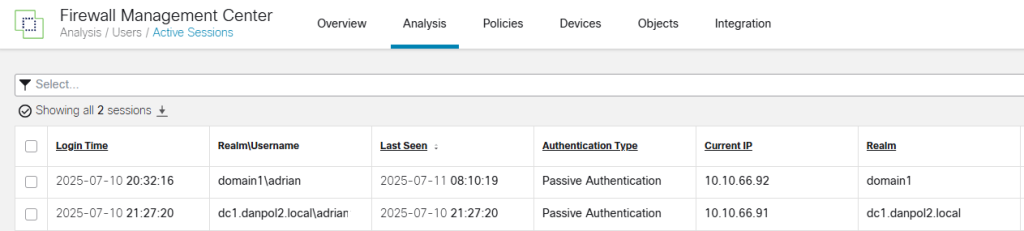
6.Build Identity policy and modify access control policy to limit traffic based on AD groups/users
Identity Policy – it is important to note that you can use 1 realm with the same criterias ,eg. if you have 2 domains using the same interface on firewall you have to use “Realm Sequences” instead of simple standard rules, like on picture.
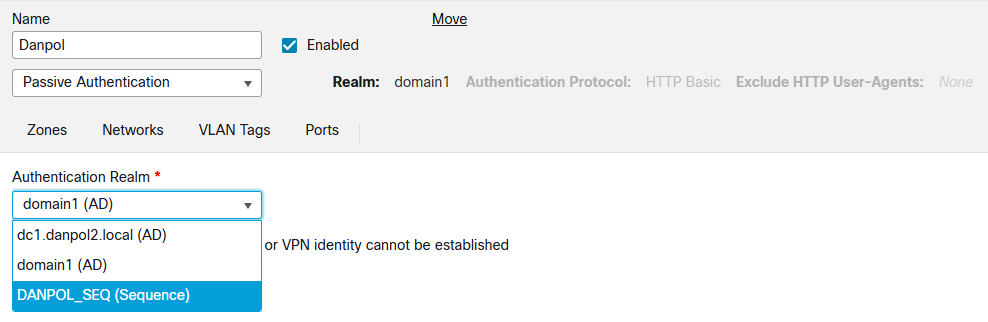
Realm Sequences define what domain is checked first but it limits you when users with the same name exists in both domains to one domain only.
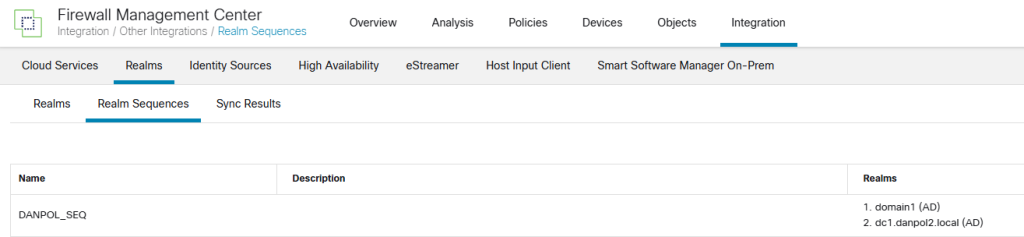
Better option is to use different interfaces for each domain or be more specific like on picture.
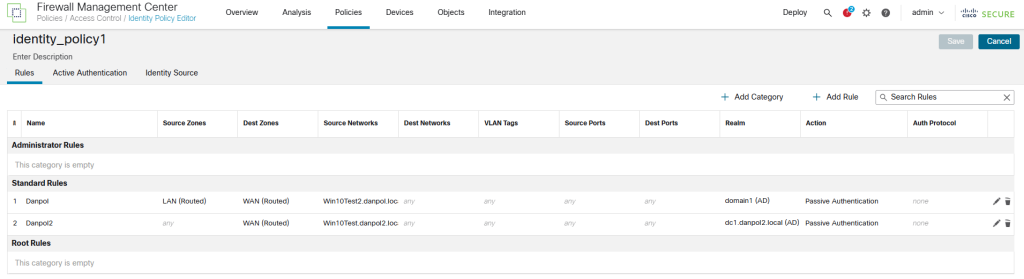
7.Define access control policy and deploy configuration to FW
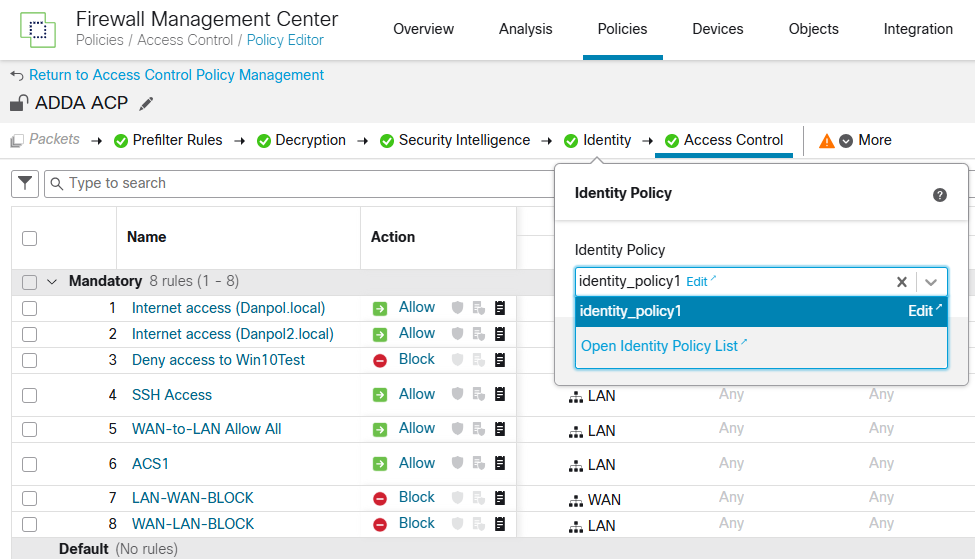
- add identity policy to access control policy
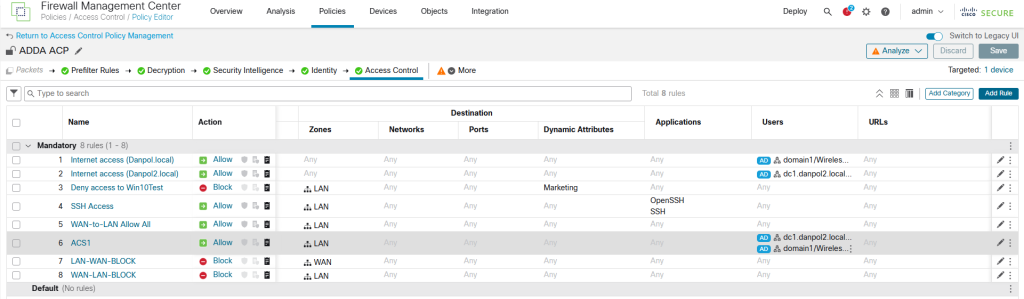
- define rules for traffic including AD groups and deploy changes
- verify traffic
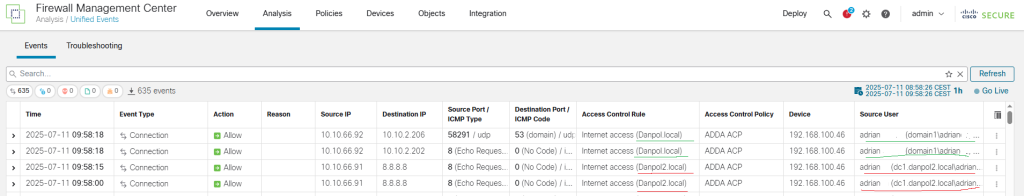
- verify again after ACP changes (Block rule)
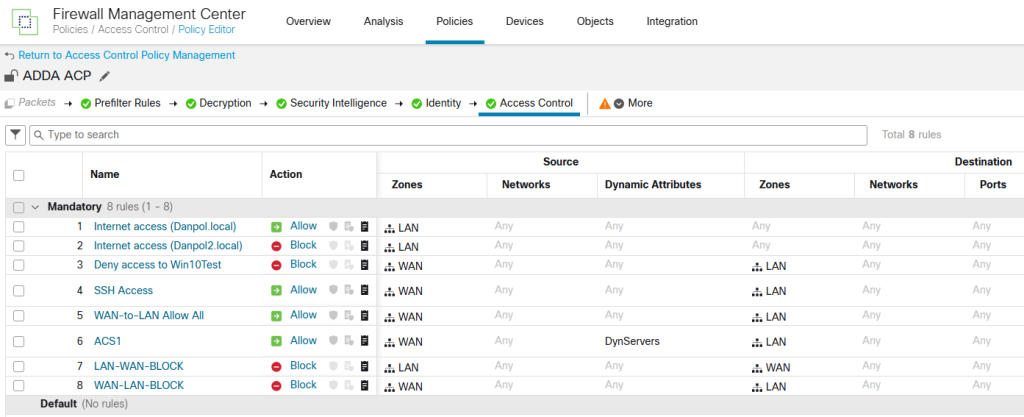
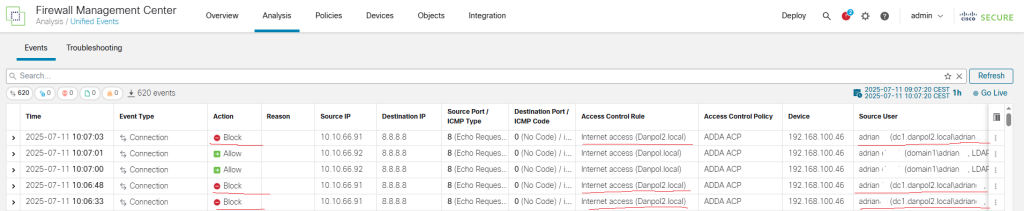
Access Control Rule confirms passive authentication is working because traffic was blocked by second rule but not rule nr7.
dzbanek 11.07.2025