Assumptions:
– ISE associated with Active Directory
– Basic ISE and Meraki Knowledge
1. WLAN (SSID) Configuration
- select WPA2 – Enterprise with my Radius server
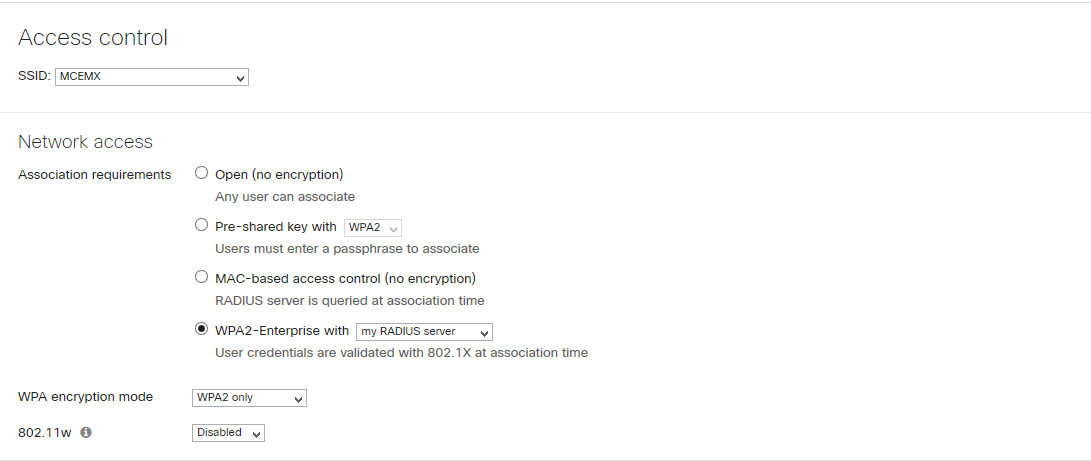
- select “Cisco Identity Services Engine (ISE) Authentication
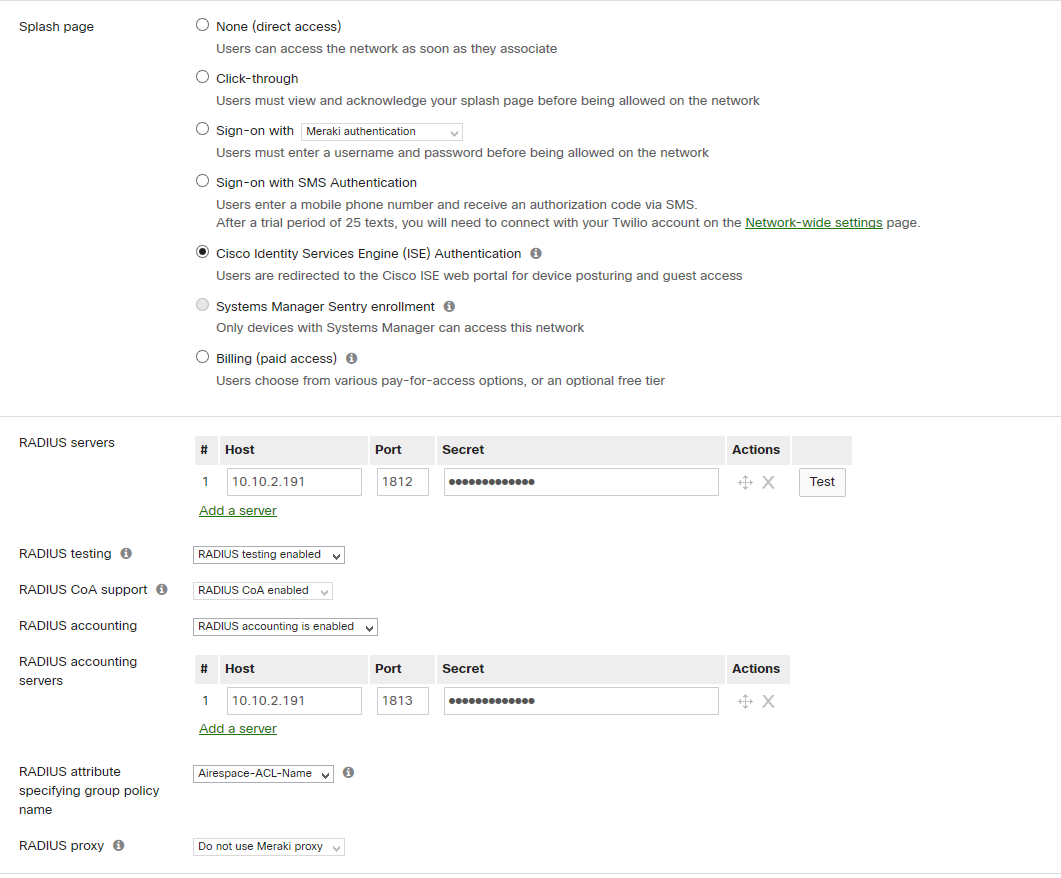
- provide ISE radius server IP (auth and acc) and PSK
- Enable CoA
- specify radius attribute “Airespace-ACL-Name” – it is needed to assign group policy for wireless users
Group policy works similar like ACL on WLC. ISE provides name of group policy(on WLC ACL name) but it does not send dACL(group policy).
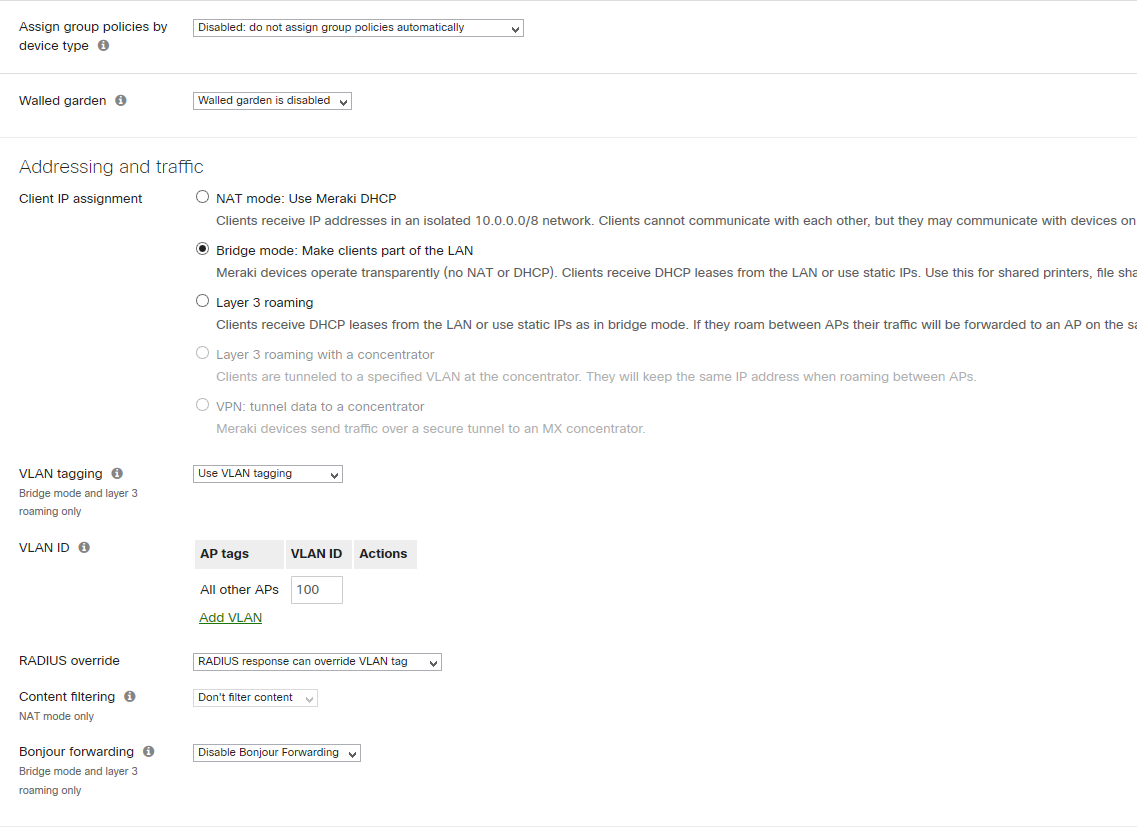
- disable group assignment policies disabled
- specify user IP assignment (in my case bridge mode)
- enable VLN tagging
- specify default VLAN ( vlan can be also dynamically assigned through ISE policies)
- enable “Radius Override”
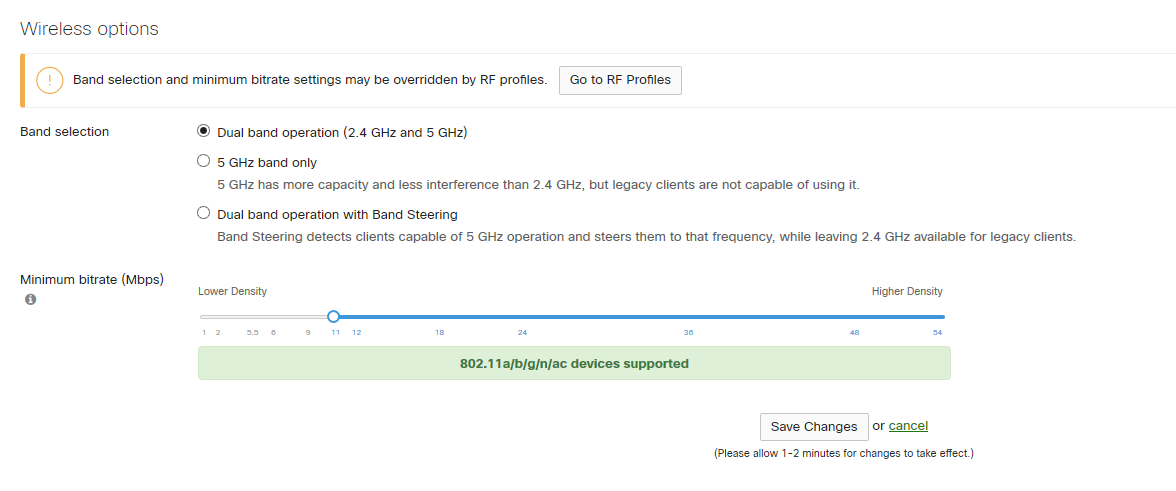
- enable 2.4GHz or 5GHz band or both
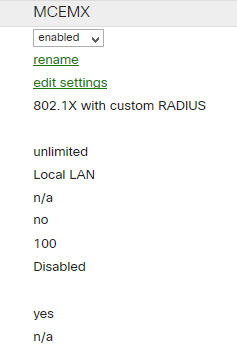
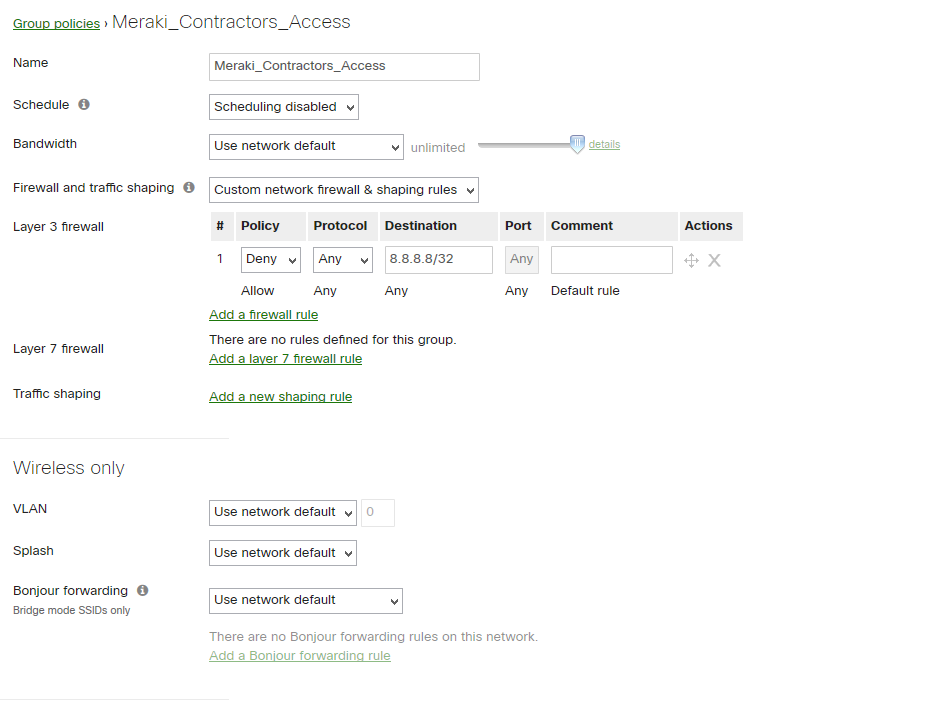
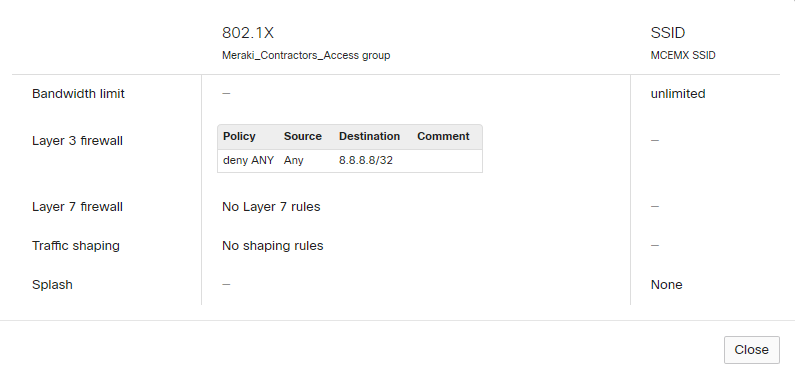
2. Configure Group Policies (for dACL assignment or/and QoS settings) – in our case name is “Meraki_Contractors_Access”
- build a L3/L7 policy
3.Configure ISE
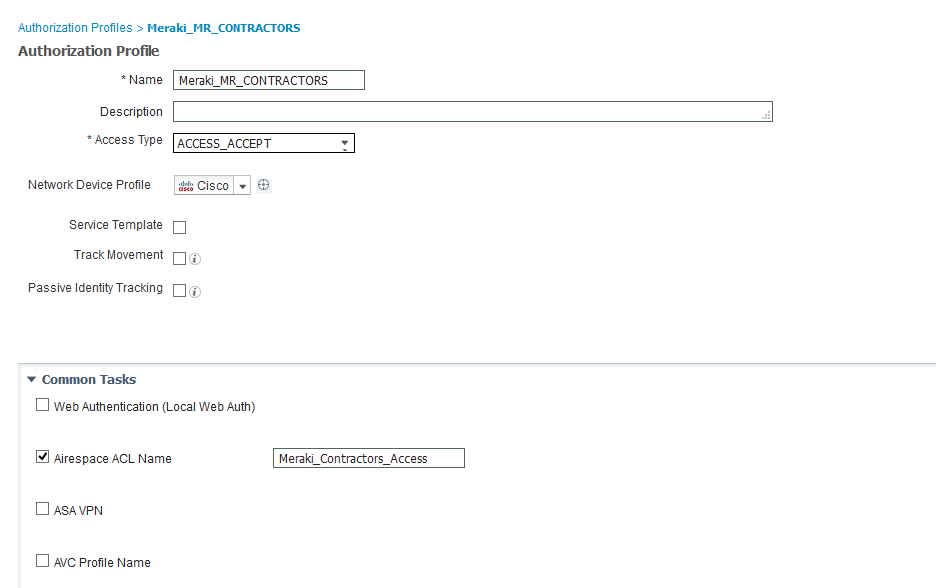
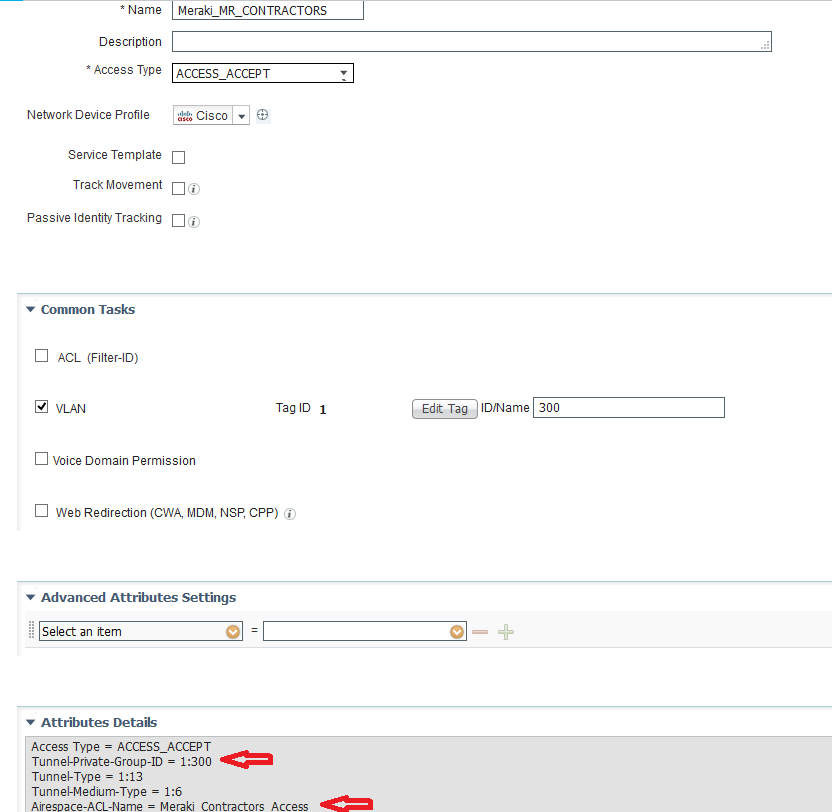
- configure authorization profile (option1 – ACL), option2 – ACL and dVlan)
option1
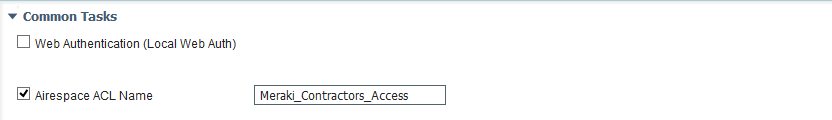
Airespace ACL Name must have the same name as group policy name on Meraki AP
option2
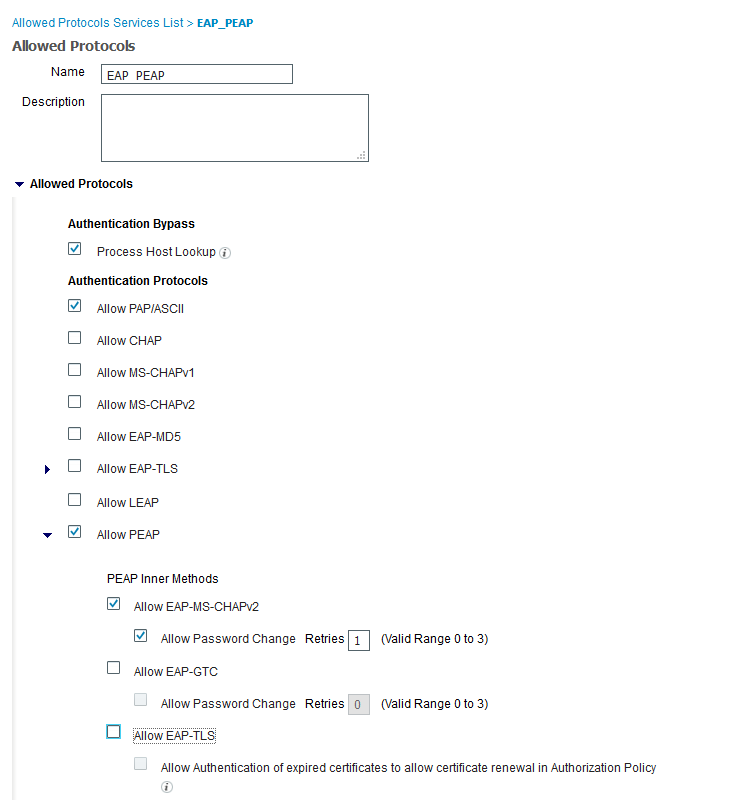
- Configure authentication protocols
I suggest to configure custom authentication protocols set but “Default Network Services” is also good choice
- Configure ISE identity source sequence (optional)
For Meraki authentication I created separate identity source sequence which uses AD credentials only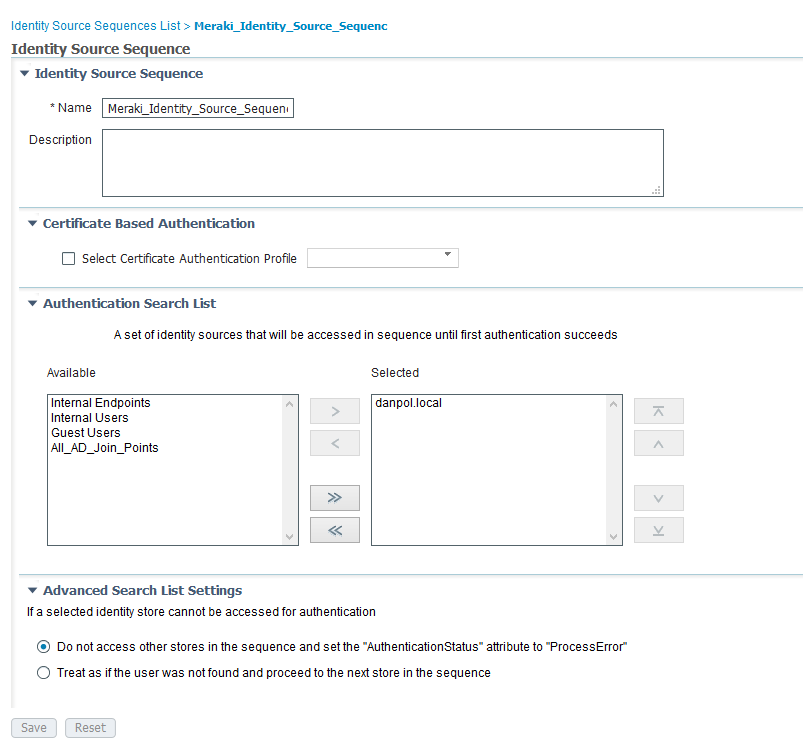
- Configure ISE policies
Authentication policy
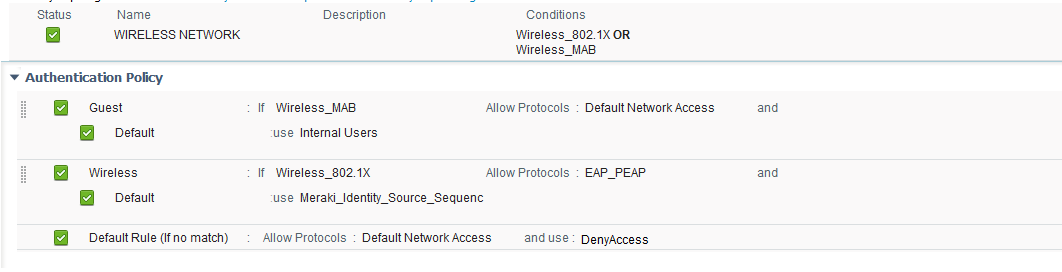
Authorization policy
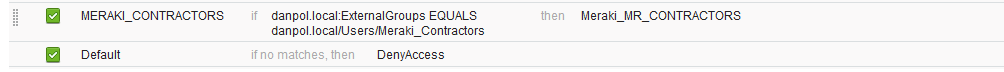
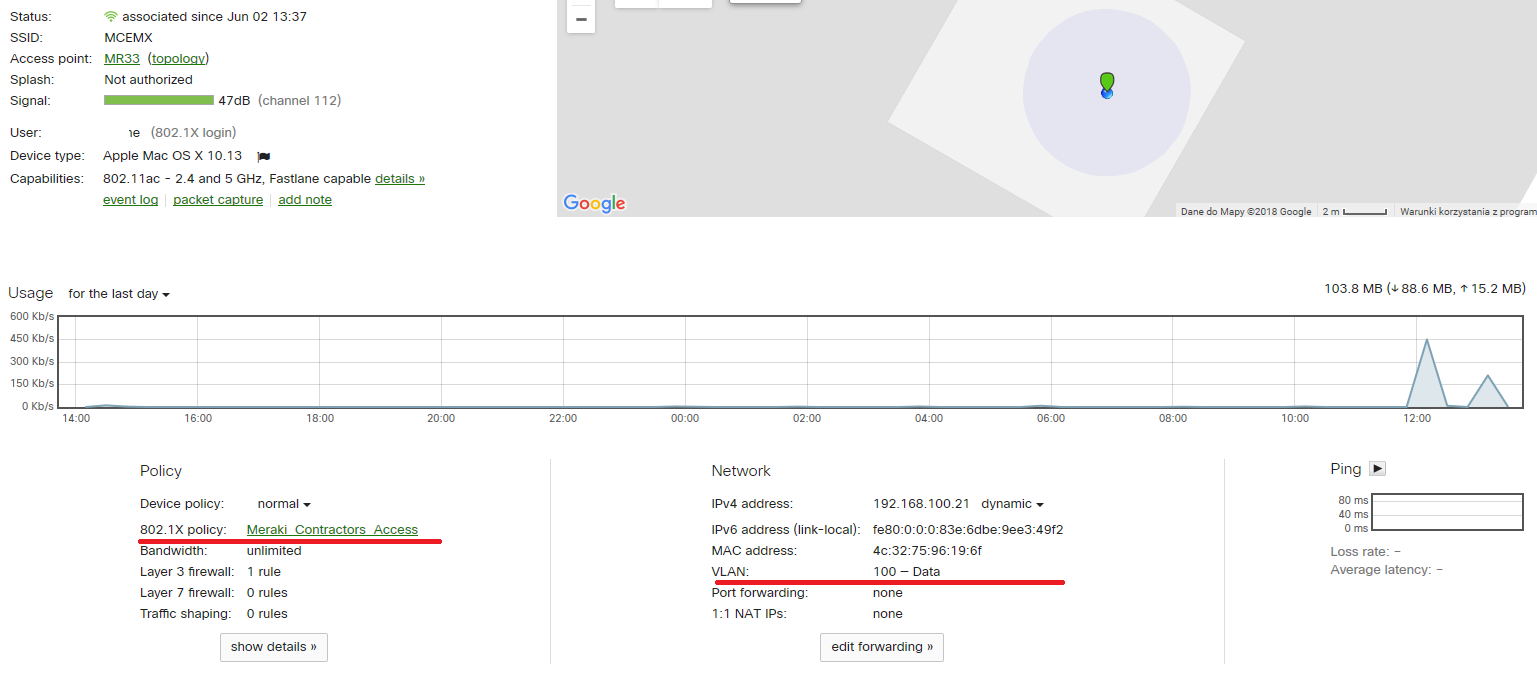
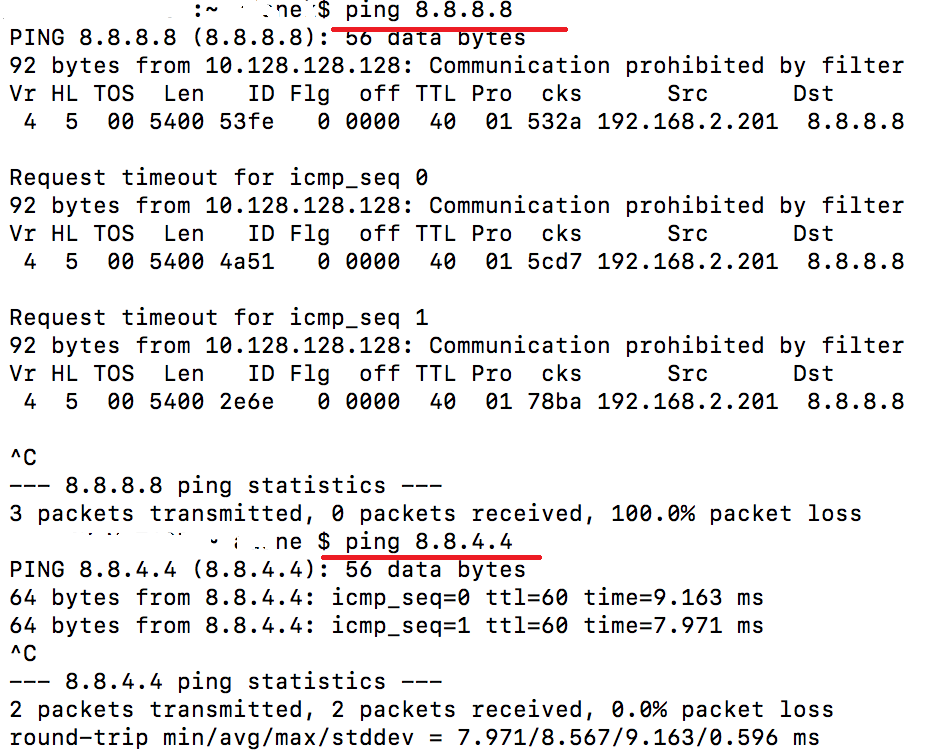
TEST 1
Group policy assignment – ACL only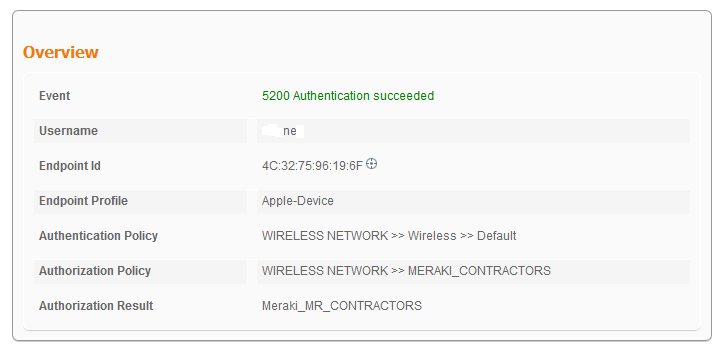
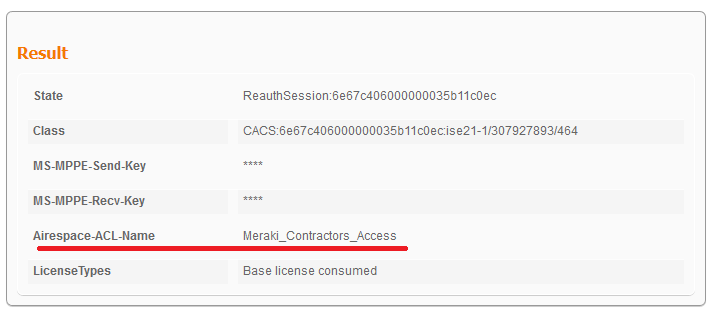
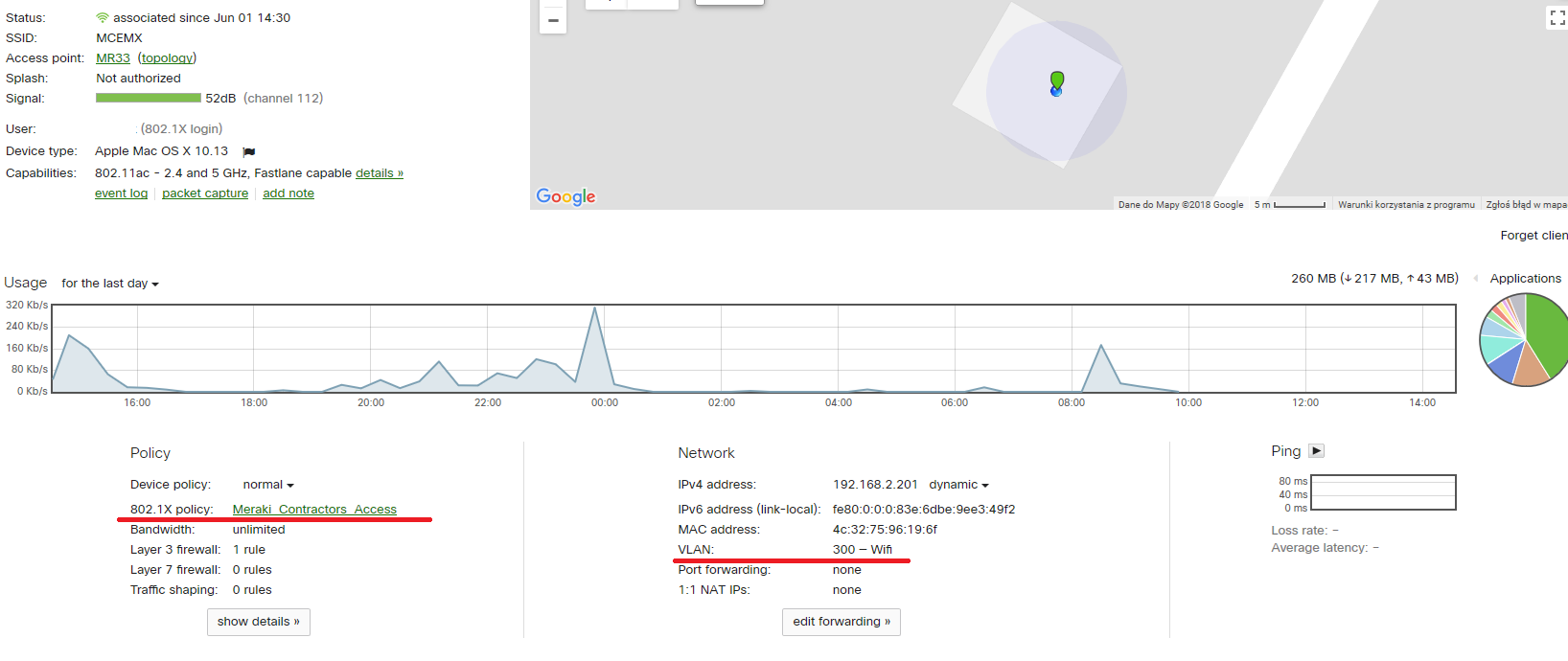
TEST 2
Group policy assignment – ACL and VLAN

dzbanek 02-06-2018