Active/Active failover is only available in multiple mode.
Assumptions:
In this manual I will only show how to configure failover but will not show how to configure contexts.
Below configuration for both ASA
ASA1
context1: abc1
GigabitEthernet0/0 nameif outside security-level 0 10.10.10.1 255.255.255.0
GigabitEthernet0/1.3 nameif inside security-level 100 10.10.30.1 255.255.255.0 vlan 300
context2: abc2
GigabitEthernet0/2 nameif outside security-level 0 172.16.1.1 255.255.255.0
GigabitEthernet0/1.1 nameif DMZ1 security-level 50 172.16.100.1 255.255.255.0 vlan 100
GigabitEthernet0/1.2 nameif DMZ2 security-level 40 172.16.200.1 255.255.255.0 vlan 200
ASA2
context1: abc1
GigabitEthernet0/0 nameif outside security-level 0 10.10.10.2 255.255.255.0
GigabitEthernet0/1.3 nameif inside security-level 100 10.10.30.2 255.255.255.0 vlan 300
context2: abc2
GigabitEthernet0/2 nameif outside security-level 0 172.16.1.2 255.255.255.0
GigabitEthernet0/1.1 nameif DMZ1 security-level 50 172.16.100.2 255.255.255.0 vlan 100
GigabitEthernet0/1.2 nameif DMZ2 security-level 40 172.16.200.2 255.255.255.0 vlan 200
UNIT 1 – ASA1
context abc1
ASA1/abc1(config)# interface gigabitEthernet 0/1.3
ASA1/abc1(config-if)# ip address 10.10.30.1 255.255.255.0 standby 10.10.30.2
ASA1/abc1(config-if)# no shutdown
ASA1/abc1(config-if)# exit
Interface GigabitEthernet0/1.3 configuration
ASA1/abc1(config)# interface gigabitEthernet 0/0
ASA1/abc1(config-if)# nameif outside
ASA1/abc1(config-if)# security-level 100
ASA1/abc1(config-if)# ip address 10.10.10.1 255.255.255.0 standby 10.10.10.2
ASA1/abc1(config-if)# no shutdown
ASA1/abc1(config-if)# exit
Interface GigabitEthernet0/0 configuration
context abc2
ASA1/abc2(config)# interface gigabitEthernet 0/1.1
ASA1/abc2(config-if)# nameif DMZ1
ASA1/abc2(config-if)# security-level 50
ASA1/abc2(config-if)# ip address 172.16.100.1 255.255.255.0 standby 172.16.100.2
ASA1/abc2(config-if)# no shutdown
ASA1/abc2(config-if)# exit
Interface GigabitEthernet 0/1.1 configuration.
ASA1/abc2(config)# interface gigabitEthernet 0/1.2
ASA1/abc2(config-if)# nameif DMZ2
ASA1/abc2(config-if)# security-level 40
ASA1/abc2(config-if)# ip address 172.16.200.1 255.255.255.0 standby 172.16.200.2
ASA1/abc2(config-if)# no shutdown
ASA1/abc2(config-if)# exit
Interface GigabitEthernet 0/1.2 configuration.
ASA1/abc2(config)# interface gigabitEthernet 0/2
ASA1/abc2(config-if)# nameif outside
ASA1/abc2(config-if)# security-level 0
ASA1/abc2(config-if)# ip address 172.16.1.1 255.255.255.0 standby 172.16.1.2
ASA1/abc2(config-if)# no shutdown
ASA1/abc2(config-if)# exit
Interface GigabitEthernet 0/2 configuration.
FAILOVER for unit1
in system context do:
ASA1(config)# failover lan unit primary
ASA1(config)# failover lan interface FAILOVER GigabitEthernet0/3
INFO: Non-failover interface config is cleared on GigabitEthernet0/3 and its subinterfaces
ASA1(config)# failover interface ip FAILOVER 192.168.1.1 255.255.255.0 standby 192.168.1.2
Asa 1 will be primary unit, GigabitEthernet 0/3 will be used for failover.
ASA1(config)# failover group 1
ASA1(config-fover-group)# primary
ASA1(config-fover-group)# exit
ASA1(config)# failover group 2
ASA1(config-fover-group)# secondary
ASA1(config-fover-group)# exit
You can configure max 2 failover groups to which you will assign contexts.
Failover group 1 on ASA 1(UNIT1) will be primary,thats is all data will be send via ASA1 for context assigned to failover group1
Failover group 2 will be secondary on ASA1 and primary on ASA2(all data will be send via ASA2 until failover will happen)
Assign failover groups to contexts
context abc1 configuration:
ASA1(config-ctx)# join-failover-group 1
ASA1(config-ctx)# exit
context abc2 configuration:
ASA1(config-ctx)# join-failover-group 2
ASA1(config-ctx)# exit
in system space enable failover:
ASA1(config)# failover
UNIT 2 – ASA2
in system space do:
ASA2(config)# failover lan unit secondary
ASA2(config)# failover lan interface FAILOVER GigabitEthernet0/3
INFO: Non-failover interface config is cleared on GigabitEthernet0/3 and its subinterfaces
ASA2(config)# failover interface ip FAILOVER 192.168.1.1 255.255.255.0 standby 192.168.1.2
Enable failover on secondary unit
ASA2(config)# failover
After few seconds replication will start between ASA appliances.
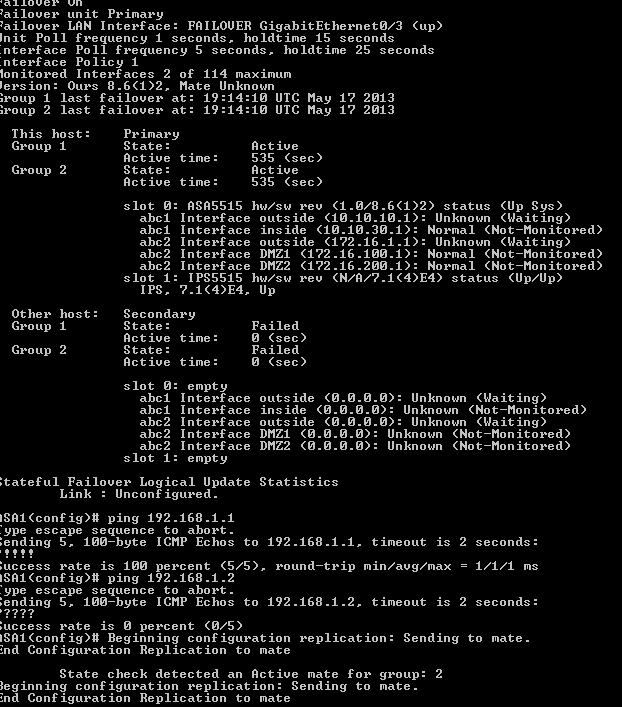
ASA1
ASA2
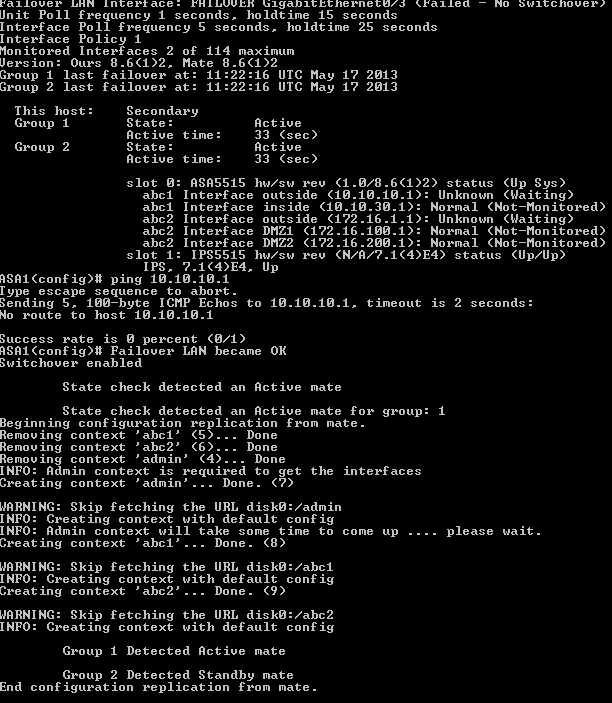
TESTS
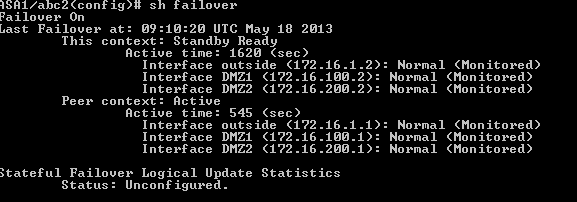
Display FAILOVER status on primary unit.
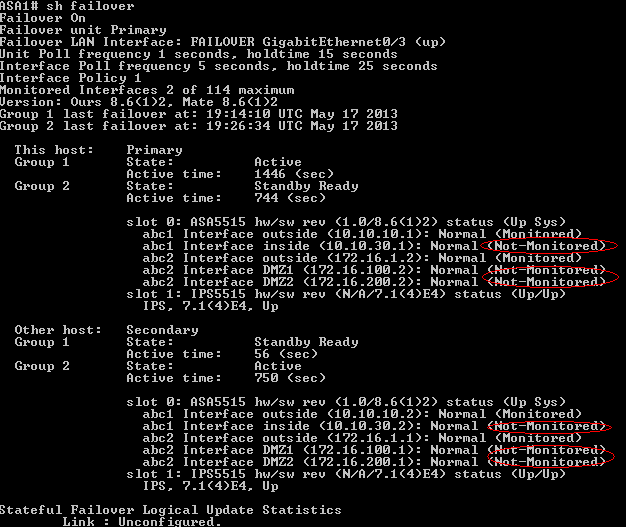
Based on output we see some interfaces are in states:
NORMAL (Monitored)
and some in
NORMAL (Not-Monitored)
Asa by default monitors physical interfaces only(NORMAL-Monitorred),to monitor also subinterfaces you have to enable them.
To do this go to context acbc1 and abc2 on ASA1.
Context abc1 on ASA1
Display monitored interfaces
ASA1/abc1(config)#show monitor-interface
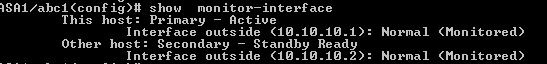
Enable “inside” interface for monitoring.
ASA1/abc1(config)# monitor-interface inside
Context abc2 on ASA1
Display monitored interfaces
ASA1/abc1(config)#show monitor-interface
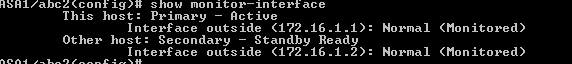
Enable DMZ1 and DMZ2 interfaces for monitoring
ASA1/abc2(config)# monitor-interface DMZ1
ASA1/abc2(config)# monitor-interface DMZ2
After a while you should see your Hadrware failover working properly.
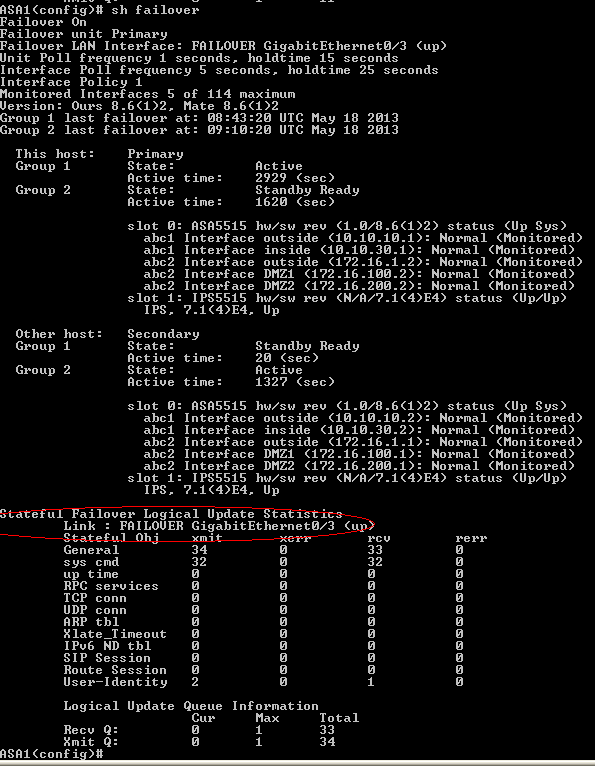
View from sytem execution space on ASA1
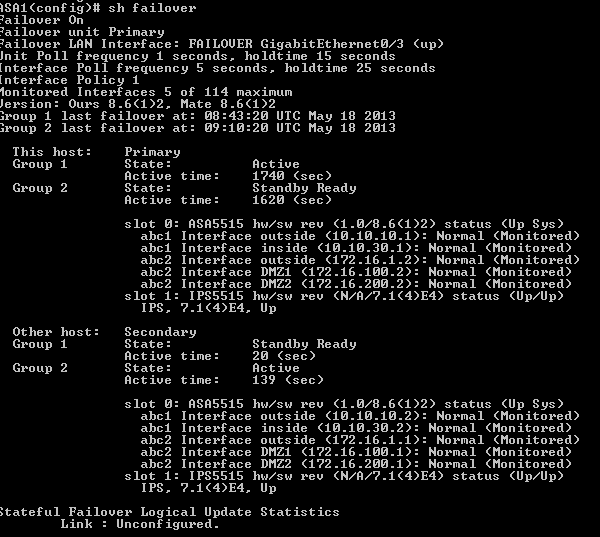
Notice ASA1 is primary unit for Failover group 1(ACTIVE state) and secondary for failover group 2(STANDBY Ready)
View from system execution space on ASA2
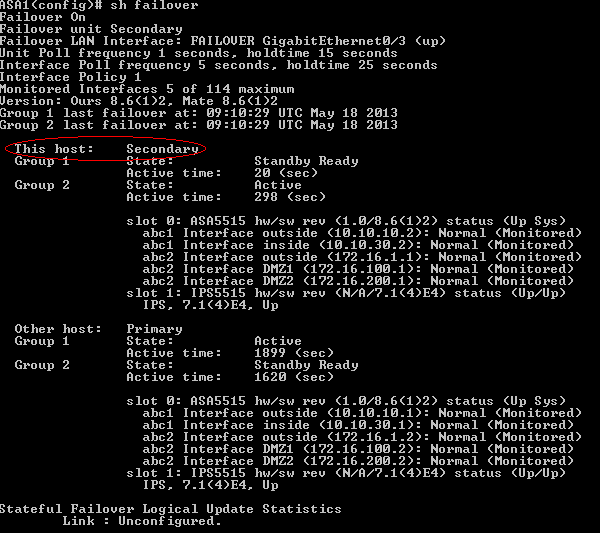
View from context abc1
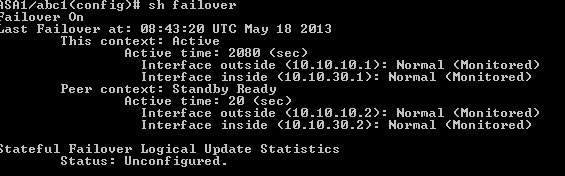
View from context abc2
From now we have 100% operational HARDWARE FAILOVER.
I strongly recommend enable also STATEFULL failover which replicate session between appliances.
Enabling Statefull failover we can do in 2 way:
1. Using separate interface and ip like in article(see here)
2.Using existing interface ,e.g. FAILOVER(for security reason do not use DATA interfaces).
Here we will enable STATEFULL failover on FAILOVER link( point 2).
Because we will use the same interface the only thing you have to do is from system execution space on ASA 1 type:
ASA1(config)# failover link FAILOVER GigabitEthernet0/3
dzbanek 2013-05-18