Assumptions:
– ISE associated with Active Directory
– Basic ISE and Meraki Knowledge
1. Access Policy configuration (name does not have to be the same like authorization profile or aaa policy)
- select “my Radius server” and provide ISE IP for AAA
- select CoA enabled
- select host-mode (single-host,muti-host, multi-auth, multi-domain) – some options are still available under beta sw release
- select acces-policy type (802.1x, Mab or both-hybrid) – 802.1x is first auth method in hybrid mode, mab starts after dot1x timeout(8secs)
- provide guest vlan(optional)
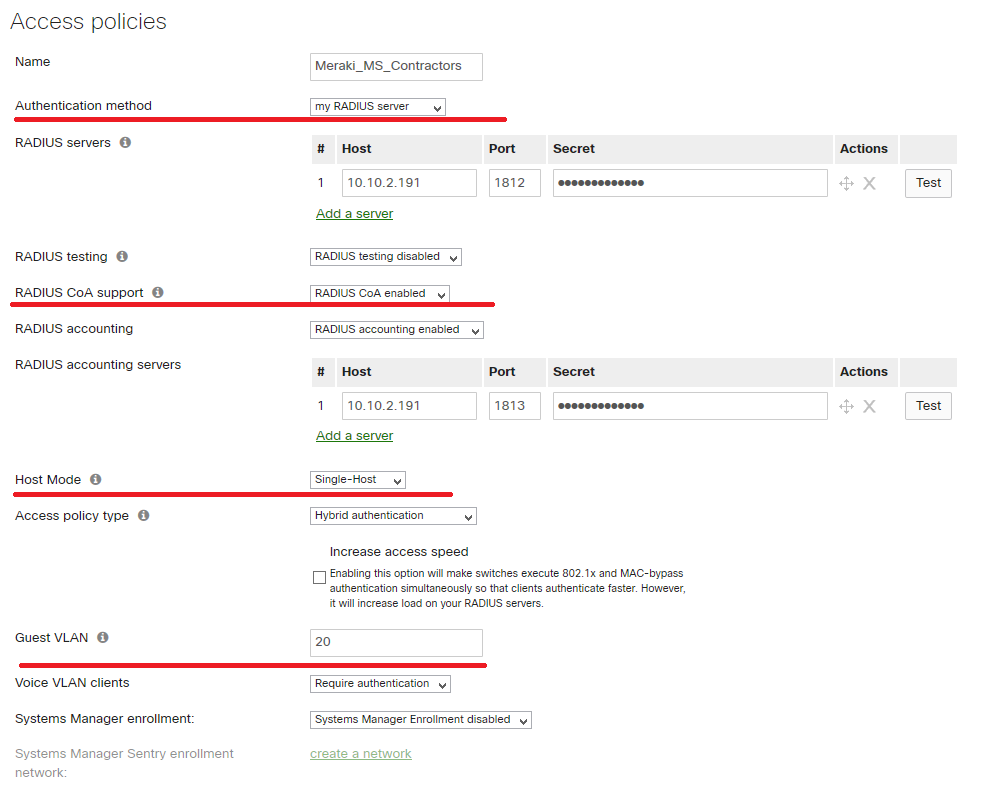
Meraki switches currently do not support dACL(may 2018), therefore ACL must be configured on switches in advance. Dynamic VLAN assignment is supported.
2. Switch ACL Configuration
ACL configured below is for test purposes only.
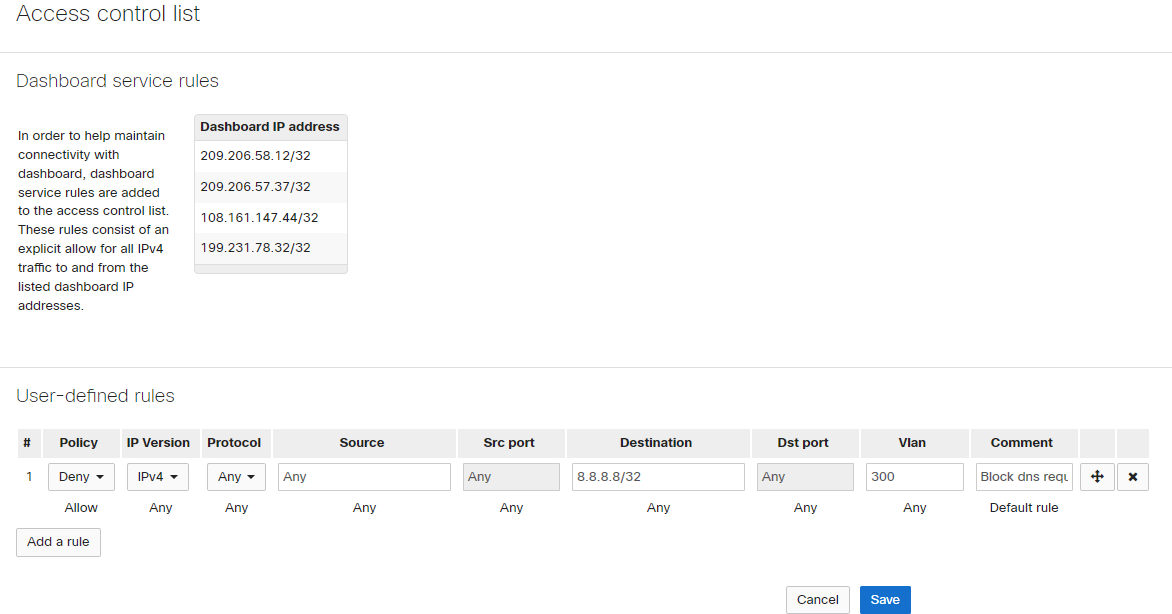
Warning!
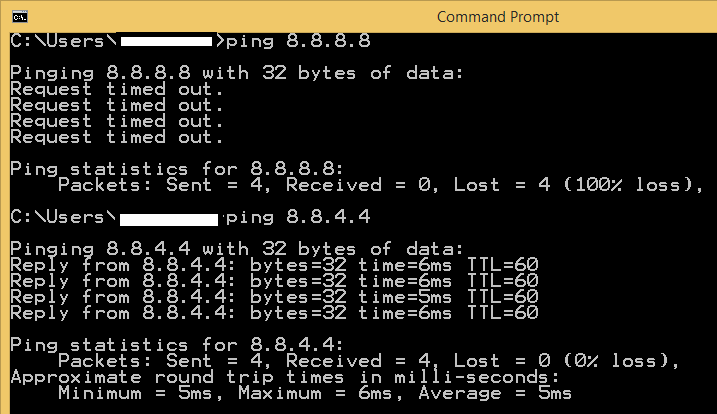
ACL rules are stateless. On example above, first rule blocks all traffic from any source on vlan 300 to host 8.8.8.8 but it does NOT block returned traffic or traffic from 8.8.8.8!!!
ACLs are deployed to all switches in domain.
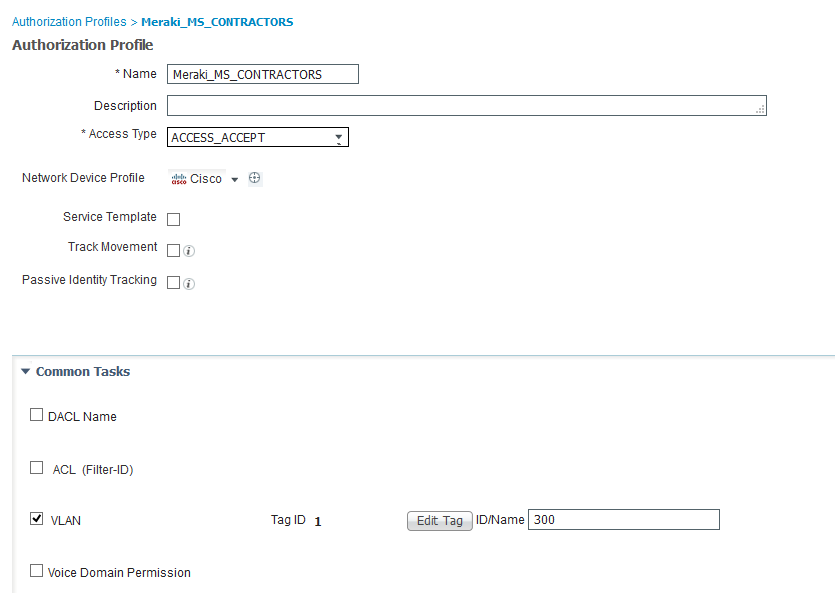
3.Configure ISE
- authorization profile
- Authentication policy
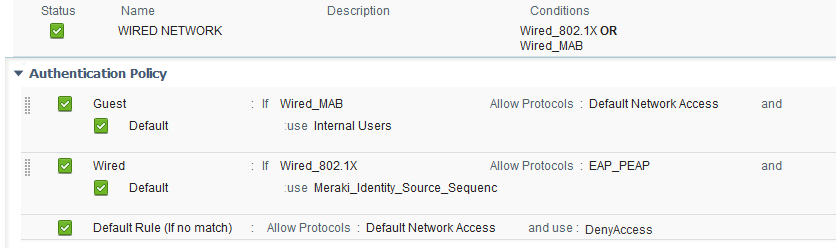
- authorization policy
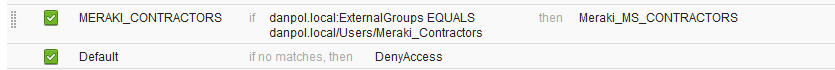
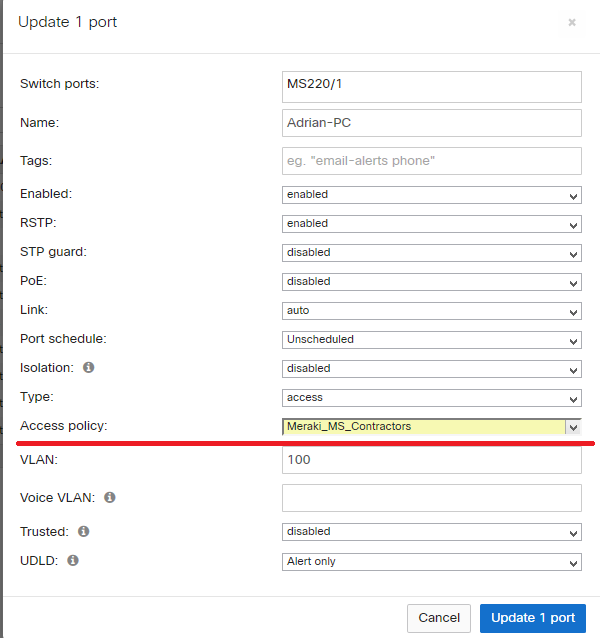
4.Assign “Meraki_MS_Contractors” policy to switchport.
Test
- ISE Live Logs

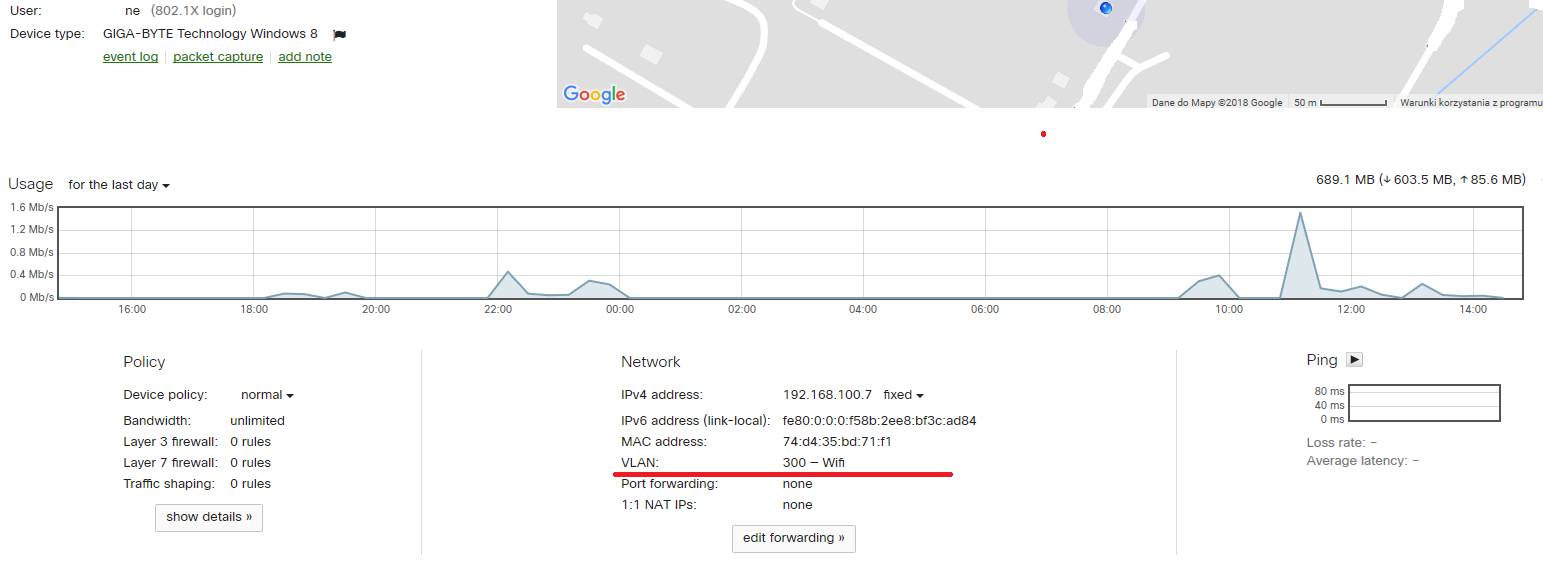
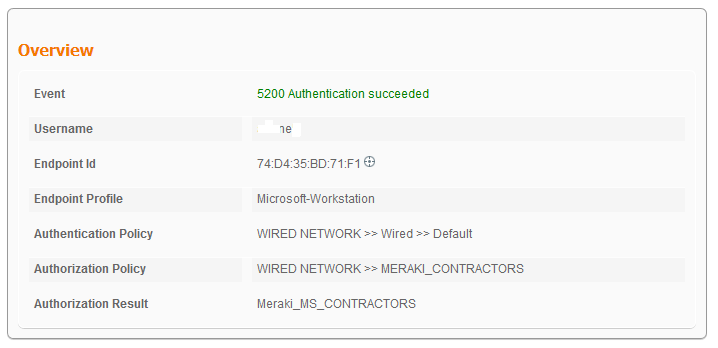
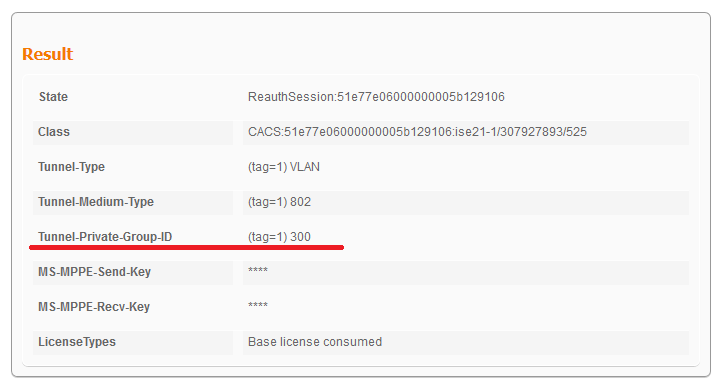
- Meraki dashbord shows dVLAN assignment(switchport is configured on Vlan100)

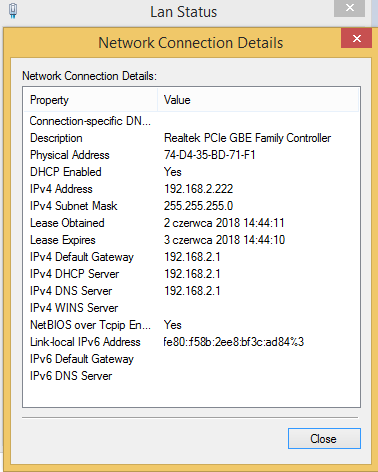
- PC Address Assignment
- ACL verification
dzbanek 02-06-2018